What's The Role Of Firewalls In Cybersecurity?
Have you ever wondered how our digital world stays safe from cyber threats? Well, let's dive into the exciting world of cybersecurity and explore the role of firewalls. So, what's the role of firewalls in cybersecurity? Let's find out!
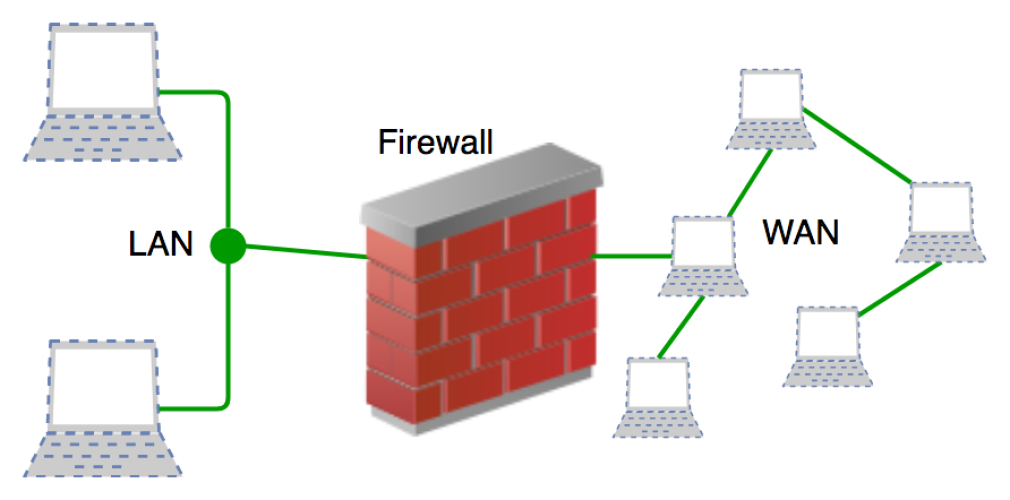
Picture this: You're the guardian of a digital castle, protecting it from malicious invaders. That's exactly what a firewall does in the world of cybersecurity. It's like a digital barrier, standing between your computer network and the wild wilderness of the internet.
Just like how a castle gatekeeper scrutinizes every person entering, a firewall carefully examines data packets entering your network, determining if they're safe or potentially harmful. It's like having a vigilant bouncer at a party, only allowing in the guests who meet your security requirements.
So, let's dive deeper into the world of firewalls and understand their crucial role in keeping our digital lives secure. Are you ready? Let's get started!

The Role of Firewalls in Cybersecurity: Protecting Against Online Threats
Firewalls play a crucial role in safeguarding computer systems and networks against cyber threats. As the digital landscape continues to expand, it becomes increasingly important to understand how firewalls contribute to cybersecurity. In this article, we will explore the functions, benefits, and types of firewalls, highlighting their pivotal role in protecting against online attacks.
Why Firewalls are Essential for Cybersecurity
Firewalls serve as the first line of defense in the ever-evolving battle against cybercriminals. By establishing a barrier between an internal network and the vast expanse of the internet, firewalls monitor incoming and outgoing traffic, analyzing and filtering data packets based on predetermined security rules. This proactive approach minimizes the risk of unauthorized access, malicious activities, and data breaches.
The Functions of Firewalls
Firewalls perform various critical functions to ensure robust cybersecurity. Firstly, they act as gatekeepers, allowing or denying access to specific network resources based on predefined security policies. Secondly, firewalls can hide internal network information from external sources, making it harder for attackers to gather sensitive data. Additionally, firewalls provide network address translation (NAT) capabilities, enabling multiple devices to share a single IP address while remaining secure.
Furthermore, firewalls can detect and prevent network intrusions through intrusion detection and prevention systems (IDPS). They constantly monitor network traffic patterns, analyzing anomalies and suspicious activity in real-time. This proactive approach allows firewalls to block potentially harmful traffic and alert network administrators to potential security breaches.
The Benefits of Using Firewalls
Implementing firewalls as part of a comprehensive cybersecurity strategy offers numerous benefits. Firstly, firewalls help establish secure perimeters, protecting internal systems, data, and confidential information from unauthorized access. They also provide businesses with increased control over network access, allowing them to define access rights and restrict individual users or groups from accessing certain resources.
Firewalls also contribute to regulatory compliance by ensuring that sensitive data is protected. Organizations that handle personal information or sensitive financial data must adhere to various security standards and regulations. Firewalls help prevent data breaches and demonstrate compliance with these regulations, reducing legal and financial risks.
In addition to these benefits, firewalls enhance network performance by optimizing network traffic flow. By filtering unwanted or malicious traffic, firewalls prevent congestion, allowing legitimate traffic to pass through smoothly. This improves overall network efficiency and user experience.
Types of Firewalls
Firewalls come in different types, each with specific characteristics and features tailored to meet various cybersecurity needs. Understanding these different types can help organizations choose the most suitable firewall solution for their requirements.
Packet Filtering Firewalls
Packet filtering firewalls operate at the network layer (Layer 3) of the OSI model. They examine individual packets based on predefined rules and determine whether to allow or block them. These firewalls are fast and efficient, but they lack the ability to inspect the content of network traffic beyond basic criteria like source and destination IP addresses.
Advantages of Packet Filtering Firewalls:
- High performance and low latency.
- Simplicity in configuration and maintenance.
- Ability to filter traffic based on a variety of criteria, including IP addresses, port numbers, and protocol types.
Disadvantages of Packet Filtering Firewalls:
- Limited ability to detect and block sophisticated attacks.
- Lack of granular control over applications or more advanced filtering options.
- Vulnerabilities to spoofing attacks due to the focus on packet headers rather than content.
Stateful Inspection Firewalls
Stateful inspection firewalls, also known as dynamic packet filtering firewalls, combine the functionality of packet filtering with additional context-awareness. These firewalls maintain a state table that tracks the state of each network connection. Upon receiving packets, they match them against the state table to ensure they belong to an established connection. This approach provides greater security and allows for more advanced rule sets.
Advantages of Stateful Inspection Firewalls:
- Enhanced security by considering the context of network connections.
- Ability to track and monitor the state of network connections, providing greater control over traffic.
- Improved resistance against spoofing attacks by verifying packet integrity.
Disadvantages of Stateful Inspection Firewalls:
- Increased resource consumption due to the maintenance of state tables.
- Limited ability to inspect encrypted traffic since the stateful inspection process occurs before decryption.
- Vulnerabilities to attacks exploiting trust relationships within established connections.
Next-Generation Firewalls (NGFW)
Next-generation firewalls combine the capabilities of traditional firewalls with advanced security features including deep packet inspection (DPI), intrusion prevention systems (IPS), application awareness, and more. NGFWs provide enhanced visibility and granular control over network traffic, enabling organizations to identify and block threats more effectively.
Advantages of Next-Generation Firewalls:
- Advanced security features that go beyond packet filtering and stateful inspection.
- Deep packet inspection enables identification of application-layer protocols and the ability to block specific applications.
- Integration of intrusion prevention systems (IPS) for real-time threat detection and prevention.
Disadvantages of Next-Generation Firewalls:
- Higher costs compared to traditional firewalls due to additional features and capabilities.
- Increased complexity, requiring more expertise for configuration and management.
- Performance degradation when applying resource-intensive features such as DPI and application control.
Choosing the Right Firewall Solution
When selecting a firewall solution, organizations should consider their specific cybersecurity requirements, budget constraints, and scalability needs. Conducting a thorough risk assessment and consulting with cybersecurity professionals can help identify the most suitable firewall type, features, and deployment options.
Considerations for Choosing a Firewall:
1. Security Requirements: Determine the level of security needed based on the organization's assets, industry regulations, and potential threats.
2. Scalability: Ensure the firewall solution can handle the organization's current needs and accommodate future growth.
3. Budget: Consider the cost of the firewall solution, including hardware, licensing, and ongoing maintenance.
4. Network Infrastructure: Understand the organization's network architecture, including the number of locations, remote access requirements, and compatibility with existing systems.
5. Security Features: Evaluate the specific security features required, such as intrusion detection and prevention, VPN support, and application control.
By carefully considering these factors, organizations can make informed decisions and implement an effective firewall solution that aligns with their cybersecurity goals.
In conclusion, firewalls are critical components of any cybersecurity strategy, acting as the first line of defense against cyber threats. With their ability to monitor, analyze, and filter network traffic, firewalls play a pivotal role in protecting sensitive data and preventing unauthorized access. By understanding the functions, benefits, and types of firewalls available, organizations can enhance their security posture and safeguard their digital assets from evolving cyber threats. Remember, keeping your network secure is an ongoing effort, and regularly updating and maintaining your firewall is crucial to effectively combat cyber risks. Stay proactive, stay vigilant, and stay protected.
Key Takeaways: What's the Role of Firewalls in Cybersecurity?
- Firewalls are a crucial part of cybersecurity.
- Firewalls act as a barrier between a trusted internal network and potential threats from the outside.
- They examine incoming and outgoing network traffic to determine if it meets certain security criteria.
- Firewalls can block unauthorized access attempts and protect against malware.
- Regular updates and maintenance of firewalls are essential for keeping up with new threats.
Frequently Asked Questions
Why are firewalls important for cybersecurity?
Firewalls play a crucial role in cybersecurity by acting as a barrier between a trusted internal network and external networks, such as the internet. They monitor and control incoming and outgoing network traffic based on predetermined security rules. This helps prevent unauthorized access to sensitive data and protects against malicious activities, such as hacking and malware attacks. Firewalls analyze the source, destination, and type of data being transmitted, filtering out potentially harmful or suspicious traffic.
Firewalls also provide an additional layer of defense by offering network address translation (NAT), which hides the internal IP addresses of devices. This adds another level of security as it makes it harder for attackers to identify and target specific devices on the network. By serving as a gatekeeper, firewalls help safeguard the network, keeping cyber threats at bay.
What types of firewalls are commonly used in cybersecurity?
There are several types of firewalls commonly used in cybersecurity. One type is the network firewall, which is a hardware or software-based solution that filters incoming and outgoing network traffic. It examines packets of data and enforces security rules to determine whether to allow or block the traffic. Another type is the host-based firewall, which is a software program that runs on an individual device and monitors its network connections. It helps protect the device from unauthorized access and malicious activities.
In addition to these, there are also application-level gateways (ALGs), which operate at the application layer of the network protocol stack. ALGs provide more granular control over specific applications or protocols, allowing organizations to define detailed security policies. Lastly, there are next-generation firewalls (NGFWs), which incorporate additional security features such as intrusion prevention systems (IPS) and deep packet inspection (DPI). These advanced firewalls go beyond traditional packet filtering and provide more robust protection against sophisticated cyber threats.
Can firewalls prevent all types of cyber attacks?
While firewalls are an essential component of a cybersecurity strategy, they cannot prevent all types of cyber attacks. Firewalls primarily focus on traffic filtering and security rule enforcement, which helps mitigate common threats like unauthorized access and malware. However, they may not be as effective against more advanced and targeted attacks.
Firewalls are unable to protect against attacks that exploit vulnerabilities within applications or devices. For instance, if a user unknowingly downloads a malicious file from the internet and executes it, the firewall may not be able to defend against the resulting malware infection. Therefore, it is crucial to complement firewall protection with other security measures, such as regular software updates, strong passwords, and employee education on safe online practices. This multi-layered approach strengthens overall cybersecurity defenses and reduces the likelihood of successful cyber attacks.
Are firewalls only necessary for businesses, or should individuals also use them?
Firewalls are not just essential for businesses; they are also necessary for individuals to protect their personal devices and information. With the increasing prevalence of online threats, such as hackers and identity theft, having a firewall in place is crucial for anyone connected to the internet.
Individuals can use firewall software on their personal computers and enable the built-in firewall features on their routers. This helps create a barrier between the internet and their devices, safeguarding them from unauthorized access and potential cyber attacks. Firewalls also help prevent outgoing connections from malicious software, providing an added layer of protection against malware spreading from the device to the network.
To ensure maximum cybersecurity, it is recommended for both businesses and individuals to regularly update their firewalls, keep their security settings robust, and stay informed about the latest cyber threats and best practices.
Can firewalls slow down network performance?
Firewalls can impact network performance to some extent, but with proper configuration and hardware capabilities, this impact can be minimized. When a firewall is enabled, it inspects incoming and outgoing traffic, which can introduce a slight delay in network transmission. However, modern firewalls are designed to perform hardware acceleration and optimize performance.
Network administrators can configure firewalls to prioritize certain types of traffic, such as critical business applications, while still maintaining security for other traffic. By customizing firewall settings, organizations can strike a balance between network performance and security. Choosing the right hardware or software solution that can handle the expected network traffic volume is also important in ensuring minimal impact on performance.
It is important to note that the benefits of having a properly configured firewall far outweigh any potential slight slowdown in network performance. By preventing cyber threats and safeguarding sensitive data, firewalls are a critical component of a comprehensive cybersecurity strategy.
What Is Firewall ? | Firewall Explained | Firewalls and Network Security | Simplilearn
Summary
Firewalls are like security guards for our devices and networks. They protect us by filtering out bad stuff and allowing only the good stuff to pass through. They can block hackers, viruses, and other threats from getting into our systems.
Firewalls can be like a barrier between us and the outside world of the internet. They check all the data that tries to come in or go out of our devices and decide if it's safe or not. They use rules and settings to decide what's allowed and what's not.
Firewalls can be software or hardware based. Software firewalls are like an app on our device, while hardware firewalls are like a special device that connects to our internet connection. Both types work together to protect us from cyber attacks and keep our information safe.
So, if you ever wonder how your computer or smartphone stays safe from online threats, it's because of firewalls doing their job to keep the bad guys out and let the good guys in.
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote