
What's The Deal With Ransomware Attacks?
Picture this: you're happily scrolling through your favorite websites, watching videos, and chatting with friends. Life is good. But then, out of nowhere, your computer freezes, and a message pops up on your screen: "Your files are encrypted. Pay us a ransom, or say goodbye to your precious data forever." What just happened? That's what we're here to explore in this article: What's the deal with ransomware attacks?
Ransomware attacks have been making headlines lately, and it's important to understand what they are and how they can affect you. You might be asking yourself, "Why would anyone do this?" Well, to put it simply, cybercriminals use ransomware to hold your files hostage and demand money in exchange for their release. It's like the digital version of kidnapping your files.
You might be thinking, "How does ransomware even get into my computer?" Great question! Ransomware can sneak into your system through various means, like opening infected email attachments, clicking on malicious links, or downloading compromised files. So it's crucial to stay vigilant and protect yourself from these cyber threats. Let's dive deeper and find out exactly how ransomware attacks work.
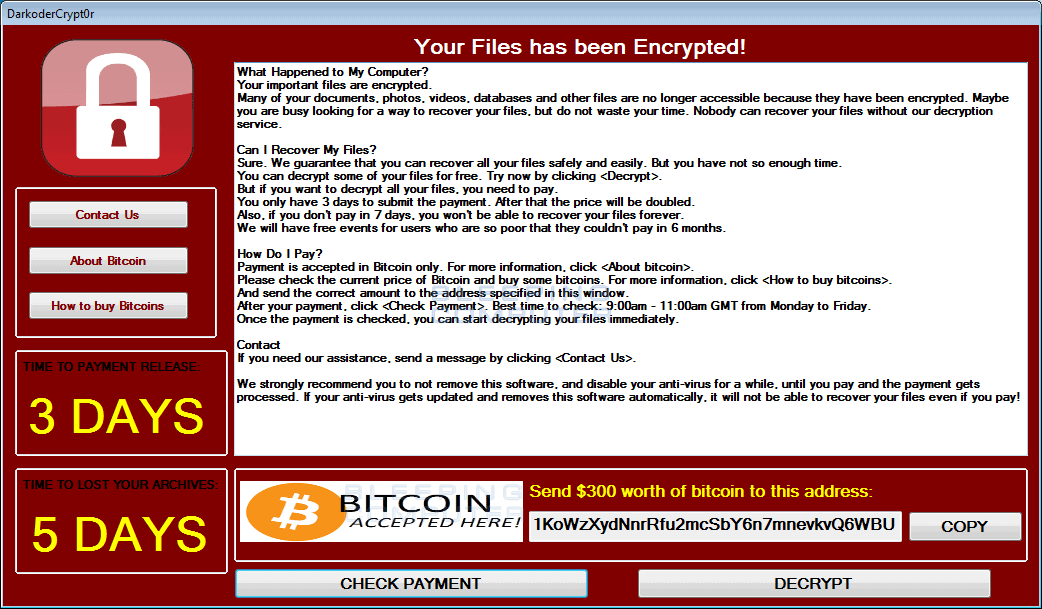
The Undeniable Impact of Ransomware Attacks
The Rise of Ransomware Attacks
Ransomware attacks have become increasingly prevalent in recent years, causing significant financial losses and operational disruptions to individuals and organizations alike. This form of cybercrime involves malicious actors encrypting victims' data or locking them out of their own systems and demanding a ransom payment in exchange for restoring access. The rapid evolution of technology and the growing reliance on digital infrastructure have created fertile ground for ransomware attacks to flourish.
One of the key factors contributing to the rise in ransomware attacks is the financial motivation behind them. Cybercriminals recognize the lucrative potential of holding critical data hostage and demand payment in cryptocurrencies, making it harder to trace the transactions. Additionally, the ease of deploying ransomware-as-a-service (RaaS) platforms has democratized cybercrime, allowing even those with limited technical skills to launch devastating attacks.
Furthermore, the COVID-19 pandemic has acted as a catalyst for ransomware attacks. With the increased reliance on remote work and digital communication, cybercriminals have exploited vulnerabilities in home networks and corporate infrastructure, capitalizing on the chaos and uncertainty that the pandemic has brought about.
The Devastating Consequences of Ransomware Attacks
The consequences of falling victim to a ransomware attack can be severe, both for individuals and organizations. Financial losses are one of the most immediate impacts, as victims often have to pay the demanded ransom to regain access to their data. In some cases, the ransom amounts can be exorbitant, especially for larger organizations that possess valuable intellectual property or sensitive customer information. Even if the ransom is paid, there is no guarantee that the attackers will honor their end of the bargain and provide the decryption key.
Operational disruptions are another significant consequence of ransomware attacks. When critical systems are locked or encrypted, businesses are unable to function properly, resulting in lost productivity, reputational damage, and potential legal ramifications. The downtime caused by these attacks can have far-reaching effects, affecting not only the targeted organization but also its customers, partners, and suppliers.
Moreover, ransomware attacks can have profound psychological and emotional impacts on the victims. The violation of privacy and the sense of powerlessness can induce stress, anxiety, and even trauma. These attacks can erode trust in technology and undermine confidence in digital systems, which are the backbone of modern society.
Preventing Ransomware Attacks: Best Practices and Mitigation Strategies
While ransomware attacks can be highly damaging, there are measures that individuals and organizations can take to reduce their risk and mitigate the impact.
1. Keep Software and Systems Up to Date:
Ransomware often exploits vulnerabilities in outdated software and operating systems. Regularly installing updates and patches helps to fortify your digital defenses and close potential entry points for attackers.
2. Implement Robust Backup Solutions:
Regularly backing up data and storing it offline can prove to be a lifesaver in the event of a ransomware attack. By maintaining offline copies, you can restore your systems without resorting to paying the ransom.
3. Educate Users About Phishing Attacks:
Phishing remains one of the primary methods used to distribute ransomware. Training employees and individuals to recognize suspicious emails, links, and attachments can significantly reduce the risk of falling victim to these attacks.
4. Establish Secure Remote Access:
Given the increased remote work landscape, ensuring secure remote access to corporate networks is essential. Implementing multi-factor authentication, robust VPN solutions, and strict access controls can help prevent unauthorized access to your systems.
5. Invest in Advanced Threat Detection and Response:
Deploying sophisticated cybersecurity solutions that employ artificial intelligence and machine learning can help detect and respond to ransomware attacks in real-time. Automated systems can swiftly identify and mitigate threats before they cause significant damage.
By adopting these best practices and continuously improving cybersecurity measures, individuals and organizations can enhance their resilience against ransomware attacks and minimize potential losses.
Understanding the Evolving Landscape of Ransomware Attacks
The Expansion of Ransomware-as-a-Service (RaaS) Platforms
The rise of ransomware attacks can be attributed in part to the proliferation of ransomware-as-a-service (RaaS) platforms. These platforms act as cybercrime marketplaces, allowing individuals with minimal technical expertise to access and deploy ransomware for their malicious purposes. RaaS models enable cybercriminals to operate at scale, offering ransomware kits and tools that are easy to use, even for those without extensive coding knowledge.
RaaS platforms operate on the dark web, providing cybercriminals with various features such as customizable ransom notes, payment systems, and even customer support. These platforms have lowered the entry barrier for aspiring ransomware attackers, leading to an increase in the number and sophistication of attacks. The as-a-service nature of RaaS has transformed ransomware attacks into a commoditized criminal industry, where individuals can purchase ready-to-use malware and launch their campaigns.
Furthermore, the development of affiliate programs within RaaS platforms has incentivized collaboration among cybercriminals. These programs allow attackers to earn a percentage of the ransom payments made by victims they refer to the platform. Such profit-sharing schemes have driven innovation and competition within the ransomware ecosystem, leading to the continuous evolution of attack methods and evasion techniques.
The Emergence of Double Extortion Attacks
Double extortion attacks have emerged as a particularly insidious variant of ransomware attacks. In addition to encrypting victims' data, attackers exfiltrate sensitive information before deploying the ransomware. This creates a dilemma for the victims, who now face not only the threat of data loss but also the risk of their stolen information being exposed or sold on the dark web.
The threat of data exfiltration gives cybercriminals additional leverage to extort victims, as they can threaten to leak or sell the stolen data if the ransom demands are not met. This two-pronged attack strategy has been highly effective, as victims are often willing to pay the ransom to prevent the release of sensitive information, even if they have backups in place.
Double extortion attacks have targeted various sectors, including healthcare, finance, and government entities. By combining data theft and ransomware, attackers maximize their potential profits and further exploit the vulnerabilities of their victims.
The Role of Emerging Technologies in Combating Ransomware
As ransomware attacks continue to evolve and become more sophisticated, the role of emerging technologies in combating this menace becomes increasingly crucial.
1. Artificial Intelligence and Machine Learning:
AI and machine learning algorithms can analyze vast amounts of data and detect patterns that indicate the presence of ransomware. These technologies enable proactive threat hunting and can help organizations stay one step ahead of evolving attacks.
2. Blockchain Technology:
Blockchain technology holds the potential to enhance cybersecurity by providing immutable and transparent records of transactions. Implementing blockchain-based solutions can help secure sensitive data and protect against ransomware attacks.
3. Quantum Computing:
While still in its nascent stages, quantum computing has the potential to revolutionize encryption algorithms. By harnessing the power of quantum computing, encryption methods used to protect data against ransomware attacks can be significantly strengthened.
The cybersecurity landscape is in a constant state of flux, and staying abreast of the latest trends and advancements in technology can provide individuals and organizations with the tools to defend against ransomware attacks effectively.
Taking a Proactive Approach to Defending Against Ransomware Attacks
Building Cyber Resilience Through Incident Response Planning
Developing a robust incident response plan is essential for organizations to effectively respond to and recover from ransomware attacks. This plan should outline the steps to be taken in the event of an attack, including isolating affected systems, notifying stakeholders, and engaging law enforcement if necessary. Regularly testing and updating the incident response plan ensures that it remains effective in the face of evolving threats.
Enhancing Employee Awareness and Training
Employees are often the first line of defense against ransomware attacks. Investing in cybersecurity awareness training programs can help educate employees about the risks, teach them to identify potential threats, and instill good security practices. Regularly updating employees on emerging attack vectors and reinforcing best practices can greatly reduce the likelihood of falling victim to a ransomware attack.
Collaborating With Industry Partners and Government Agencies
It is crucial for organizations to share threat intelligence and collaborate with industry peers and government agencies to effectively combat ransomware attacks. Through information sharing mechanisms, organizations can stay informed about emerging threats and benefit from collective defense strategies.
Adopting a Defense-in-Depth Security Strategy
A defense-in-depth security strategy involves layering multiple security controls to protect against ransomware attacks. This approach includes implementing firewalls, intrusion detection systems, endpoint protection, and vulnerability management solutions. By applying a multi-layered approach, organizations can significantly reduce their exposure to ransomware attacks.
Conducting Regular Security Assessments
Regularly assessing and testing the security posture of an organization can help identify vulnerabilities and areas of weakness that could be exploited by ransomware attacks. Conducting penetration testing, vulnerability scanning, and security audits ensures that the organization's defenses remain robust and up to date.
By implementing these proactive strategies and maintaining a vigilant stance against ransomware attacks, individuals and organizations can protect their digital assets and mitigate the devastating impacts of these malicious acts.
Staying One Step Ahead: The Future of Ransomware Defense
The Importance of Cybersecurity Education
With the ever-evolving nature of ransomware attacks, cybersecurity education is crucial for individuals of all ages. By teaching cybersecurity awareness and best practices from a young age, we can equip the next generation with the knowledge and skills necessary to mitigate the risks posed by ransomware and other cyber threats.
Advancements in Artificial Intelligence and Automation
Artificial intelligence and automation are poised to play a significant role in the future of ransomware defense. These technologies can rapidly identify and respond to emerging threats, autonomously detect and neutralize ransomware, and provide real-time insights to cybersecurity professionals.
The Role of Government and Legislation
Effective legislation and government initiatives are crucial in combatting ransomware attacks. Governments need to work collaboratively with industry experts to develop comprehensive frameworks that address the rapidly evolving threat landscape. By enforcing stricter penalties for cybercriminals and fostering international cooperation, governments can create a more secure digital environment for individuals and organizations.
The battle against ransomware attacks is ongoing, but by investing in education, leveraging emerging technologies, and fostering partnerships between industry and government, we can empower ourselves to stay one step ahead of these malicious actors. Together, we can build a more secure and resilient digital future.
Key Takeaways: What's the Deal with Ransomware Attacks?
1. Ransomware attacks are a type of cybersecurity threat that can hold your computer files hostage.
2. Hackers demand money from victims in return for access to their files.
3. These attacks can happen to anyone, so it's important to be vigilant and protect yourself.
4. Regularly backing up your files and using strong passwords can help prevent ransomware attacks.
5. It's crucial to update your software and be cautious of suspicious emails or websites to stay safe from ransomware.
Frequently Asked Questions
Ransomware attacks are a growing concern in the digital world. Below are some common questions and answers to help you understand what's the deal with ransomware attacks.
How do ransomware attacks work?
Ransomware attacks typically start when a user unknowingly downloads or opens a malicious file or link, often disguised as a legitimate file or email attachment. Once the ransomware gains access to the victim's system, it encrypts the files, making them inaccessible. The attackers then demand a ransom, usually in the form of cryptocurrency, in exchange for the decryption key that will unlock the files.
Ransomware attacks can occur through various means, including phishing emails, malicious websites, or exploiting vulnerabilities in software. It's essential to stay vigilant and keep your computer systems and software up to date to prevent falling victim to ransomware attacks.
What motivates attackers to carry out ransomware attacks?
The primary motivation behind ransomware attacks is financial gain. Attackers see potential profits in extorting money from individuals, businesses, or organizations by encrypting their files and demanding a ransom for their release. Typically, attackers request payment in cryptocurrencies like Bitcoin or Monero, which provide a certain level of anonymity and make it harder to trace the transactions back to them.
While financial gain is the primary motivation, some attackers may target specific industries or organizations for political or ideological reasons. These attacks can cause widespread disruption, damage reputations, or compromise sensitive data as a form of protest or to advance a specific agenda.
How can I protect myself from ransomware attacks?
There are several steps you can take to protect yourself from ransomware attacks. First and foremost, regularly backup your important files and data to an external hard drive or cloud storage. This way, even if your files are compromised, you can restore them without paying the ransom.
Additionally, it's crucial to keep your operating system and all software up to date, as updates often patch vulnerabilities that ransomware exploits. Be cautious when opening email attachments or clicking on links, especially those from unknown sources. Implement strong and unique passwords, use two-factor authentication wherever possible, and invest in reliable antivirus and anti-malware software to detect and prevent ransomware infections.
What should I do if I become a victim of a ransomware attack?
If you become a victim of a ransomware attack, it's essential to remain calm and follow these steps. Disconnect your computer from the network to prevent further spread of the ransomware. Report the incident to law enforcement and provide them with any information related to the attack. Take screenshots of any ransom messages as evidence.
Do not pay the ransom immediately. Consult with a cybersecurity professional who can assess the situation and explore potential solutions. In some cases, decryption tools may be available to help recover your files without paying the ransom. Finally, once you have resolved the issue, strengthen your security measures to prevent future attacks.
Are there any notable ransomware attacks in recent years?
Yes, several high-profile ransomware attacks have occurred in recent years. One notable example is the WannaCry attack in 2017, which affected hundreds of thousands of computers worldwide. Another is the Colonial Pipeline attack in May 2021, where a ransomware attack resulted in a temporary shutdown of the largest fuel pipeline in the United States.
These attacks highlight the significant impact ransomware can have on critical infrastructure and everyday operations. They serve as a wake-up call to individuals and organizations to remain vigilant and take proactive steps to protect against ransomware attacks.
Should you worry about ransomware attacks? Explained
Summary
Ransomware attacks are when bad guys take over your computer and demand money from you. They can get in through email or by tricking you into clicking on something. To avoid getting attacked, make sure to have strong passwords and be careful about what you click on.
If you do get attacked, don't panic. Disconnect from the internet and report it to an adult. Remember, prevention is key, so stay alert and stay safe online!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote