What Is Social Engineering And How To Defend Against It?
Welcome, young reader, to a fascinating journey into the world of social engineering and how to defend against it. You may wonder, "What is social engineering?" and "Why is it important to protect ourselves?" Well, get ready to uncover the answers and arm yourself with the knowledge to stay safe in this digital age.
So, what exactly is social engineering? In simple terms, it's a clever manipulation technique used by cybercriminals to trick people into revealing sensitive information or performing actions they normally wouldn't. Think of it as a real-life game of deception, where hackers exploit human psychology rather than hacking into systems directly.
Now, you might be wondering, "How can I defend against social engineering?" Don't worry, young friend, we've got you covered! By learning about common social engineering tactics, being aware of the red flags, and following a few simple guidelines, you can protect yourself and your personal information from falling into the wrong hands.
So, fasten your seatbelt and get ready to embark on this eye-opening journey where you'll uncover the secrets of social engineering and discover the tools you need to defend yourself. Let's dive in and learn how to outsmart the tricksters and keep our digital lives secure!
1. Stay vigilant and be aware of social engineering techniques.
2. Be cautious with suspicious emails and messages.
3. Keep your personal information private.
4. Use strong and unique passwords.
5. Regularly update your software and antivirus programs.
6. Educate yourself and your employees about social engineering.
Remember, defending against social engineering requires a combination of awareness, caution, and proactive measures.
What Is Social Engineering and How to Defend Against It?
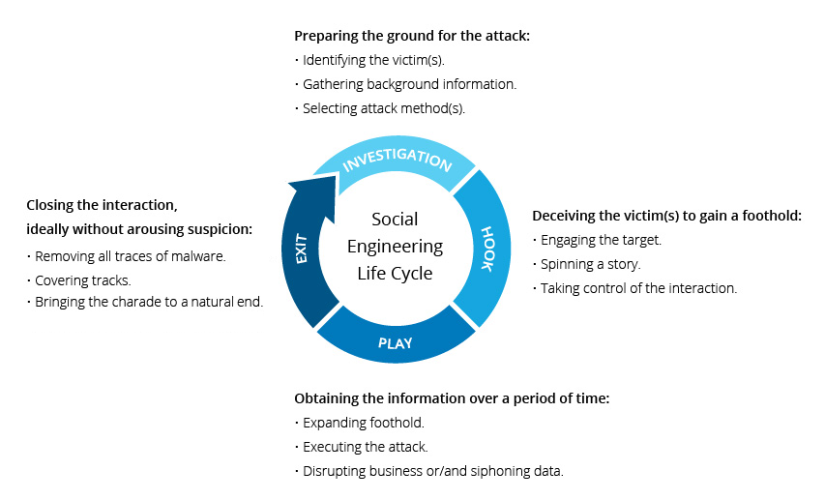
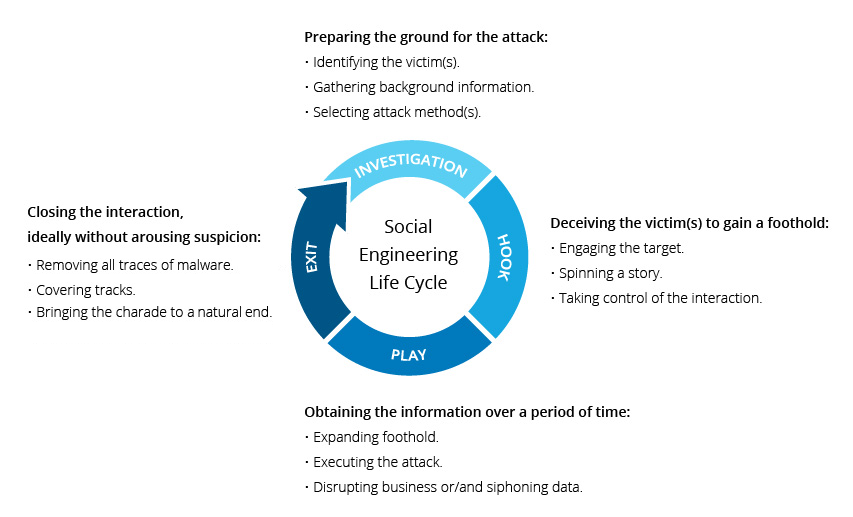
Social engineering is a form of manipulation and deception that aims to exploit human psychology to gain unauthorized access to sensitive information or resources. It involves tricking individuals into divulging confidential details or performing actions that are against their best interests. Social engineering attacks can take various forms, such as phishing emails, impersonation, baiting, and pretexting.
To defend against social engineering, it is crucial to educate yourself about the different tactics used by attackers and take proactive measures to protect your personal information. By understanding the techniques employed by social engineers and implementing security best practices, you can significantly reduce the risk of falling victim to these types of attacks.
The Psychology Behind Social Engineering
Understanding Human Behavior
Human behavior plays a significant role in social engineering attacks. Social engineers exploit common psychological traits and emotions, such as trust, authority, curiosity, and fear, to manipulate victims into revealing sensitive information or performing harmful actions. They use persuasive techniques to create a sense of urgency, confusion, or legitimacy to deceive their targets.
The Power of Pretexting
Pretexting is a social engineering technique that involves creating a false pretext to manipulate others into providing sensitive information or performing actions they wouldn't typically do. Social engineers may pretend to be from a trusted entity or use a believable story to gain the victim's confidence. By establishing a credible pretext, attackers can manipulate individuals into divulging personal information, such as passwords, credit card numbers, or social security numbers.
The Role of Phishing and Impersonation
Phishing is one of the most common social engineering techniques used by attackers. It involves sending fraudulent emails or messages that appear to be from reputable organizations or individuals. These emails often contain links to fake websites or attachments that contain malware. Impersonation is another aspect of social engineering, where attackers pretend to be someone else to deceive their targets. This could involve impersonating a colleague, a service provider, or a trusted entity to gain access to sensitive information.
Tips for Defending Against Social Engineering Attacks
1. Awareness and Education
One of the most effective ways to defend against social engineering is to be aware of the tactics used by attackers. Stay informed about the latest social engineering techniques and educate yourself and your team members about the risks. Regularly conduct security awareness training to raise awareness about the importance of protecting sensitive information and the potential consequences of falling victim to social engineering attacks.
2. Verify Requests and Sources
Before providing any sensitive information or performing requested actions, always verify the source. Do not blindly trust emails, phone calls, or messages from unknown or suspicious sources. Use official contact information obtained independently to reach out to the organization or individual in question. Be cautious of urgent or high-pressure requests, as these are common tactics used by social engineers to exploit emotions and rush decision-making.
3. Use Strong and Unique Passwords
Ensure that you use strong, unique passwords for all your online accounts. Avoid using easily guessable information such as birthdays or names. Consider using a password manager to generate and store complex passwords securely. Additionally, enable two-factor authentication whenever possible, as it adds an extra layer of security to your accounts.
Protecting Yourself in the Digital Age
4. Keep Your Software Updated
Regularly update your devices and software to ensure you have the latest security patches and protection against known vulnerabilities. Attackers often target outdated software to exploit security weaknesses and gain unauthorized access to systems or information.
5. Be Cautious of Suspicious Links and Attachments
Exercise caution when clicking on links or opening attachments, especially if they are from unknown senders or seem suspicious in any way. Hover over links to see the destination URL before clicking on them. If you're unsure about the legitimacy of an attachment or link, contact the sender directly to verify its authenticity.
6. Report Suspected Social Engineering Attacks
If you suspect that you have encountered a social engineering attack or received a phishing email, report it to the appropriate authorities. Your report can help prevent others from falling victim to similar attacks.
In conclusion, social engineering attacks can have severe consequences, both personally and professionally. By understanding the tactics used by social engineers and implementing security best practices, you can significantly reduce the risk of becoming a victim. Stay informed, be cautious, and report any suspicious activity to protect yourself and others from social engineering attacks.
Key Takeaways: What Is Social Engineering and How to Defend Against It?
- Social engineering is a method used by hackers to manipulate people and trick them into revealing sensitive information.
- Always be cautious of suspicious emails, phone calls, or messages requesting personal information.
- Avoid clicking on unfamiliar links or downloading attachments from sources you don't trust.
- Regularly update your passwords and enable two-factor authentication for added security.
- Stay informed about common social engineering techniques and educate your friends and family to help them stay safe too.
Frequently Asked Questions
Here are some common questions about social engineering and how to defend against it:
1. What is social engineering?
Social engineering is a technique used by attackers to manipulate people into revealing sensitive information or performing actions that they wouldn't normally do. It involves psychological manipulation rather than technical hacking. The attackers exploit human weaknesses, such as trust, curiosity, or fear, to gain unauthorized access to data or systems.
For example, a social engineer might pose as a trustworthy person, like a colleague or a customer service representative, and trick someone into sharing their passwords or financial information. Social engineering attacks can take various forms, such as phishing emails, phone calls, or even in-person interactions.
2. How can I recognize a social engineering attack?
Social engineering attacks can be cleverly disguised and difficult to detect, but there are some warning signs to look out for. Be cautious if you receive unsolicited requests for personal information, especially if they come through unexpected channels like email, phone calls, or social media. These requests may ask for passwords, financial details, or other sensitive data.
Another red flag is a sense of urgency or fear created by the attacker. They may pressure you to act quickly or make you believe that dire consequences will occur if you don't comply. Additionally, be skeptical of requests for information that seems unnecessary or unusual. When in doubt, it's always a good idea to verify the authenticity of the request through a trusted channel, such as contacting the organization directly.
3. How can I protect myself against social engineering?
There are several steps you can take to defend yourself against social engineering attacks. First, be aware of the tactics used by social engineers and educate yourself about common attack methods. By understanding the techniques they employ, you can be more alert and less likely to fall for their tricks.
Second, never share sensitive information unless you are certain about the legitimacy of the request. Be cautious when clicking on links or opening attachments in emails, especially if they are from unknown sources. It's important to have up-to-date security software on your devices to protect against malware and phishing attempts.
4. What should I do if I suspect a social engineering attack?
If you suspect that you are being targeted by a social engineering attack, it's important to trust your instincts. Do not share any personal information or perform any requested actions. Disconnect from any suspicious communication channels and report the incident to the appropriate authorities, such as your IT department or the organization being impersonated.
It's also a good idea to change your passwords immediately, especially if you've already fallen victim to the attack. Be sure to monitor your accounts and financial statements for any signs of fraudulent activity. Lastly, share your experience with others to raise awareness and help prevent others from falling for the same tricks.
5. How can organizations defend against social engineering attacks?
Organizations can take various measures to defend against social engineering attacks. It starts with employee education and training, teaching staff to be vigilant and recognize the signs of a potential attack. Regularly conducting simulated social engineering exercises can help identify vulnerabilities and provide an opportunity for further training.
In addition, implementing strict access controls and authentication protocols can help prevent unauthorized access to sensitive information. Organizations should also establish clear policies regarding the handling of sensitive data and ensure that all employees are aware of and follow these policies. Regularly updating security software and systems and conducting thorough audits of processes can also help identify and address any potential weaknesses.
Detecting and Defending Social Engineering Attacks
Summary
Social engineering is when cybercriminals trick people into giving them personal information or access to their devices. They use tactics like pretending to be someone trustworthy or creating a sense of urgency. To defend against social engineering, we need to be cautious and skeptical of suspicious requests or unexpected messages. It's important to verify the identity of the person or organization before giving them any sensitive information. We should also keep our devices and passwords secure, and regularly update our software to stay protected. By being aware and taking these precautions, we can avoid falling victim to social engineering attacks.
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote