What Is IT Auditing?
What is IT auditing? Have you ever wondered how companies ensure that their computer systems are secure and their data is protected? Well, that's where IT auditing comes in. It's like having a detective for technology, making sure everything is running smoothly and guarding against potential risks.
IT auditing involves reviewing and evaluating an organization's IT infrastructure, processes, and controls to ensure they comply with industry standards and regulations. It's like taking a close look at the inner workings of a computer system to make sure everything is in order.
In this article, we'll uncover the world of IT auditing, exploring what it entails, its importance in today's digital landscape, and how it helps keep organizations safe from cyber threats. So, let's dive in and discover the fascinating realm of IT auditing together!
An IT audit is a comprehensive examination of an organization's information technology infrastructure, systems, and processes. It involves assessing the effectiveness, efficiency, and security of IT systems to ensure they meet industry standards and regulatory requirements. IT auditors evaluate controls, assess risks, and provide recommendations for improvement. By conducting IT audits, organizations can identify vulnerabilities and weaknesses in their IT systems and implement strategies to mitigate these risks. This helps safeguard sensitive data and maintain the integrity and confidentiality of information.

Understanding IT Auditing: Safeguarding Information Security
IT auditing is a crucial process that helps organizations ensure the security and integrity of their information systems. In this digital age, where data breaches and cyber threats are becoming increasingly prevalent, IT auditing plays a vital role in identifying vulnerabilities, strengthening controls, and mitigating risks. This article provides an in-depth exploration of IT auditing, its significance, methodologies, and best practices.
The Importance of IT Auditing
In today's interconnected world, organizations heavily rely on technology to store, process, and transmit sensitive information. This reliance exposes them to numerous risks, including data breaches, unauthorized access, and system failures. IT auditing acts as a proactive measure to identify and address these vulnerabilities before they are exploited by malicious actors. By conducting regular audits, organizations can evaluate the effectiveness of their information security policies, assess compliance with regulations and industry standards, and make informed decisions to improve their overall security posture.
The Process of IT Auditing
IT auditing typically involves a comprehensive evaluation of an organization's IT infrastructure, systems, and processes. The following paragraphs outline the key steps of the IT auditing process.
Planning: Before initiating an IT audit, auditors define the scope, objectives, and methodologies of the audit. This includes identifying the specific systems or processes to be audited, establishing the audit timeline, and assembling the necessary resources.
Risk Assessment: The auditor conducts a thorough risk assessment to identify potential vulnerabilities and risks associated with the organization's IT environment. This involves analyzing the current security controls, assessing the likelihood and impact of potential threats, and prioritizing areas of concern.
Testing and Evaluation: Auditors perform various tests to evaluate the effectiveness of the organization's controls and processes. This may include testing system configurations, reviewing access controls, assessing the vulnerability management program, and checking for compliance with applicable regulations.
Reporting: Once the audit is complete, the auditor prepares a detailed report that outlines their findings, identifies areas of concern, and provides recommendations for improvement. This report is then shared with the organization's management, who are responsible for implementing the suggested changes.
Methods and Techniques Used in IT Auditing
IT auditors employ various methods and techniques to conduct their assessments effectively. Some commonly used methods include:
1. Compliance Auditing: This type of audit focuses on evaluating the organization's adherence to regulatory and legal requirements. It ensures that the organization complies with relevant laws, regulations, and industry standards.
2. Control Self-Assessment: Also known as a self-audit, this method involves organizations performing their own internal audits to assess their control environment. This approach encourages accountability and allows for ongoing monitoring of controls.
3. Vulnerability Assessment: This technique aims to identify weaknesses and vulnerabilities in an organization's IT infrastructure. By scanning and analyzing the network, auditors can pinpoint potential entry points for malicious actors and recommend remedial actions.
4. Penetration Testing: This method involves attempting to exploit vulnerabilities in the organization's systems to determine the effectiveness of its security controls. By simulating real-world attacks, auditors can assess the vulnerability of the systems and identify areas that require strengthening.
5. IT General Controls Review: This type of audit evaluates the organization's overall IT control environment, including policies, procedures, and the management of IT resources. It ensures that appropriate controls are in place to safeguard the organization's information systems.
IT auditing is a critical process that enables organizations to maintain the confidentiality, integrity, and availability of their information assets. By regularly assessing the effectiveness of their controls and addressing potential vulnerabilities, organizations can enhance their overall security posture and minimize the risk of data breaches, system failures, and other security incidents.
Benefits of Effective IT Auditing
Enhanced Security
One of the primary benefits of IT auditing is the enhanced security it provides to organizations. By conducting regular audits, organizations can identify weaknesses and vulnerabilities in their IT systems, helping them strengthen their controls and safeguard against potential threats. This, in turn, reduces the risk of data breaches, unauthorized access, and other security incidents.
Compliance with Regulations and Standards
Organizations are subject to various regulations and industry standards that govern the collection, storage, and processing of sensitive information. IT auditing ensures that organizations comply with these requirements, helping them avoid costly penalties and reputational damage. By identifying any gaps in compliance and implementing necessary measures, organizations can demonstrate their commitment to data protection and privacy.
Improved Operational Efficiency
IT auditing not only helps organizations identify security vulnerabilities but also highlights areas where operational efficiencies can be improved. By assessing IT processes, controls, and resources, auditors can identify redundant or outdated practices and recommend streamlined solutions. This can lead to cost savings, increased productivity, and improved overall performance.
Enhanced Stakeholder Confidence
Effective IT auditing provides stakeholders, including customers, investors, and regulators, with confidence in an organization's ability to protect their information. By demonstrating a commitment to strong information security practices, organizations can build trust and credibility, which are increasingly important in today's data-driven business environment.
Continuous Improvement
IT auditing is not a one-time activity; it is an ongoing process that organizations should incorporate into their overall risk management framework. By regularly conducting audits and addressing any identified weaknesses, organizations can continuously improve their information security practices and adapt to evolving threats and technologies.
Best Practices for IT Auditing
Stay Up-to-Date with Technological Advancements
As technology rapidly evolves, it is essential for IT auditors to stay informed about the latest advancements and emerging threats. This allows them to assess the appropriateness of existing controls and recommend necessary updates to address new risks.
Adopt a Risk-Based Approach
IT auditors should prioritize their efforts based on the organization's risk profile. This involves identifying critical systems and processes, assessing the potential impact of vulnerabilities, and focusing on areas with the highest likelihood and potential consequences of exploitation.
Collaborate with Information Security Professionals
During the auditing process, it is crucial for IT auditors to collaborate with information security professionals within the organization. This collaboration ensures that the audit aligns with the organization's overall security strategy and that any identified vulnerabilities are appropriately addressed.
Maintain Independence and Objectivity
To ensure the integrity and impartiality of the audit process, IT auditors must maintain independence from the systems and processes being audited. This includes avoiding conflicts of interest and maintaining objectivity when reporting findings and making recommendations.
Document Audit Findings and Recommendations
It is essential to document all audit findings and recommendations accurately. This documentation serves as a record of the assessment and provides a basis for tracking progress, implementing changes, and demonstrating compliance with regulations and standards.
Stay Abreast of Regulatory Requirements
IT auditors must keep themselves updated with relevant regulatory requirements and industry standards. This ensures that the audit process remains aligned with current expectations and enables organizations to maintain compliance with applicable laws and regulations.
Continuously Improve Audit Practices
IT auditors should actively seek feedback, stay informed about emerging best practices, and engage in professional development opportunities. Continuous improvement in audit practices ensures that the auditing process remains effective and relevant in an ever-changing technological landscape.
In conclusion, IT auditing is a vital process for organizations looking to protect their sensitive information and ensure the integrity of their systems. By evaluating controls, identifying vulnerabilities, and making recommendations, IT auditors play a critical role in addressing existing risks and preventing future security incidents. Implementing best practices and staying proactive in auditing efforts can significantly enhance an organization's overall security posture and provide stakeholders with confidence in its ability to protect valuable information.
Key Takeaways: What is IT Auditing?
- IT auditing is the process of evaluating an organization's IT systems and controls.
- It helps to ensure the reliability and integrity of data, policies, and procedures.
- IT auditors assess IT infrastructure, security measures, and system vulnerabilities.
- They identify risks and recommend improvements to enhance efficiency and minimize potential threats.
- IT auditing plays a crucial role in maintaining compliance with legal and industry regulations.
Frequently Asked Questions
Welcome to our FAQ section where we'll answer some common questions about IT auditing. Whether you're new to the field or looking to expand your knowledge, we're here to help!
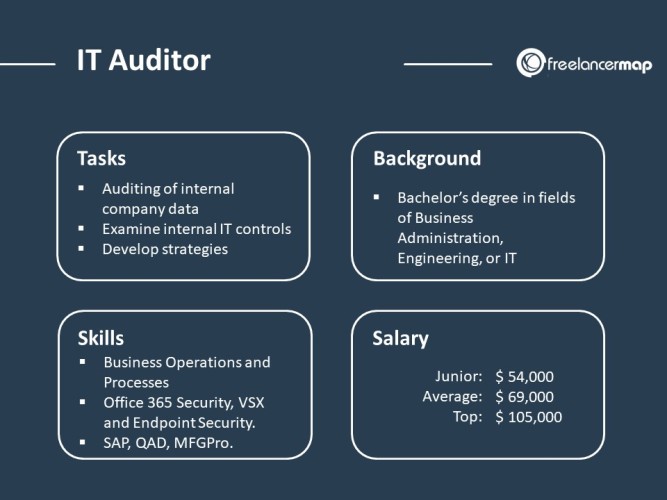
1. What is the role of an IT auditor?
An IT auditor is responsible for evaluating an organization's IT systems, processes, and controls to ensure they are efficient, secure, and comply with industry regulations. They assess risks, identify weaknesses, and recommend improvements to enhance the overall performance and security of IT infrastructure.
IT auditors work closely with internal teams and external stakeholders to conduct thorough reviews, perform data analysis, and provide recommendations to enhance IT governance, risk management, and compliance frameworks. Their goal is to help organizations operate smoothly and securely in the digital age.
2. How does IT auditing benefit organizations?
IT auditing offers numerous benefits to organizations. Firstly, it helps ensure the integrity, confidentiality, and availability of critical data and information systems. By identifying vulnerabilities and weaknesses, IT auditors help mitigate the risks of cybersecurity threats, data breaches, and unauthorized access.
Additionally, IT auditing enhances operational efficiency by assessing the effectiveness of IT processes and controls. By identifying areas for improvement, organizations can streamline their IT operations, reduce costs, and enhance overall productivity. Moreover, IT auditing helps organizations comply with industry regulations and standards, protecting them from legal and financial risks.
3. What qualifications are required to become an IT auditor?
To become an IT auditor, a strong foundation in IT and information security is essential. A bachelor's degree in computer science, information systems, or a related field is often required. Additionally, professional certifications such as Certified Information Systems Auditor (CISA) or Certified Information Systems Security Professional (CISSP) are highly valued.
Experience in IT auditing, risk management, or cybersecurity is also beneficial. Strong analytical skills, attention to detail, and the ability to effectively communicate complex technical information are crucial for success in this field. Continuous learning and staying updated with industry trends and advancements are also important for IT auditors.
4. What is the difference between internal and external IT auditing?
Internal IT auditing refers to the practice of assessing an organization's IT systems, processes, and controls by an internal team of auditors. These auditors are employees of the organization and are familiar with its systems and operations. Internal IT auditors provide independent assessments to promote internal controls and risk management.
On the other hand, external IT auditing is conducted by independent auditing firms or consultants who are not employed by the organization. External auditors bring unbiased perspectives and expertise from working with various organizations. They provide objective evaluations and assurance to stakeholders, including regulatory authorities and investors.
5. How often should IT audits be conducted?
The frequency of IT audits depends on various factors, including the size of the organization, industry regulations, and the complexity of IT systems. Generally, IT audits should be conducted at regular intervals to ensure ongoing compliance and to assess any changes or updates in IT infrastructure.
Annual IT audits are common for many organizations. However, in rapidly evolving industries or organizations with high cybersecurity risks, more frequent audits may be necessary. It is important to establish a risk-based approach to determine the appropriate frequency of IT audits, taking into consideration the organization's specific requirements and the dynamic nature of technology.
Summary
IT auditing is like checking a computer's health. It helps make sure everything is safe and working properly. Auditors check for problems, like viruses or hackers, and make recommendations to keep things secure. They also help make sure that computer programs follow rules and do what they're supposed to.
In IT auditing, auditors review computer systems to find problems and keep things running smoothly. They make sure that information is safe and that computers are working correctly. Auditors also help improve security and make sure that computer programs are following the rules. It's like being a detective for computers and making sure they stay out of danger!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote