What Are Zero-Day Vulnerabilities, And How To Handle Them?
Picture this: you're cruising through the digital world, exploring websites and apps, when suddenly, a cyber threat strikes! It's called a zero-day vulnerability, and it gives hackers a secret entryway into your digital life. But fear not, young cyber explorer, because in this adventure, we're going to uncover what zero-day vulnerabilities are and learn how to handle them. So buckle up and get ready to dive into the exciting world of cybersecurity!
Now, you might be wondering, "What are zero-day vulnerabilities anyway?" Well, imagine if you discovered a hidden passage in a fortress that even the guards didn't know about. That's what a zero-day vulnerability is—an undiscovered weakness in an app, program, or operating system that hackers exploit before anyone has a chance to fix it. It's like they've discovered a secret backdoor that allows them to sneak in without anyone noticing.
But don't worry, we're not defenseless against these cunning cyber criminals. In fact, that's exactly what we'll be exploring in this journey. We'll uncover the secrets of detecting and protecting ourselves against zero-day vulnerabilities. So, put on your cybersecurity cape and get ready to become a hero in the digital world!
Zero-day vulnerabilities are undisclosed software flaws that can be exploited by attackers before developers have a chance to patch them. Handling such threats requires a proactive approach. Regularly update software, employ robust firewall protection, and use intrusion detection tools. Additionally, network segmentation and user education play vital roles in mitigating risks. Stay vigilant, as zero-day vulnerabilities can have severe consequences, including data breaches and system compromise.

What Are Zero-Day Vulnerabilities, and How to Handle Them?
Welcome to our guide on zero-day vulnerabilities and how to effectively handle them. In today's digital age, where cyber threats are constantly evolving, zero-day vulnerabilities pose a significant risk to individuals, businesses, and organizations. These vulnerabilities refer to software flaws or weaknesses that are unknown to the software developer and can be exploited by hackers for malicious purposes. Understanding the nature of zero-day vulnerabilities and implementing robust strategies to protect against them is crucial in maintaining cybersecurity.
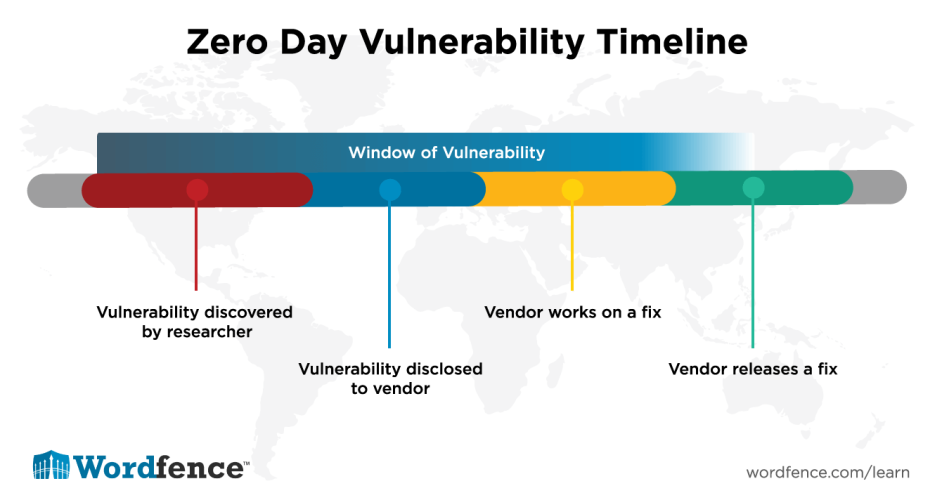
What Are Zero-Day Vulnerabilities?
Zero-day vulnerabilities are software vulnerabilities that are discovered by hackers before the software developer becomes aware of them. These vulnerabilities are named 'zero-day' because developers have zero days to fix them before they are exploited. In other words, there is no patch or update available to address the vulnerability when it is first discovered. This knowledge gap between discovery and mitigation creates a window of opportunity for attackers to exploit the vulnerability and carry out cyberattacks.
Zero-day vulnerabilities can exist in various types of software, including operating systems, web browsers, plugins, and applications. Attackers leverage these vulnerabilities to gain unauthorized access, steal sensitive data, plant malware, or launch other malicious activities. Once the software developer becomes aware of the vulnerability, they work quickly to develop and release a patch or update to fix the issue. However, until the fix is implemented, the vulnerability remains a serious threat.
It is worth noting that zero-day vulnerabilities are highly valuable to attackers due to their stealthy nature. Since these vulnerabilities are unknown to developers, traditional cybersecurity solutions such as antivirus software may not detect the attacks. This makes it even more crucial for organizations and individuals to take proactive measures to protect themselves against zero-day attacks.
The Impact of Zero-Day Vulnerabilities
The discovery and exploitation of zero-day vulnerabilities can have severe consequences for individuals and organizations. Here are some of the potential impacts:
1. Data Breaches: Zero-day vulnerabilities can be used to gain access to sensitive data, such as personally identifiable information (PII) or corporate intellectual property. This data can then be sold on the dark web or used for fraudulent activities.
2. Financial Loss: Zero-day attacks can lead to direct financial loss, especially for businesses. Attackers may steal funds, conduct unauthorized transactions, or demand ransoms to restore access to compromised systems or data.
3. Reputation Damage: A successful zero-day attack can tarnish the reputation of organizations, erode customer trust, and lead to long-term business consequences.
4. Operational Disruption: Zero-day attacks can disrupt critical operations by compromising systems, networks, or infrastructure. This may result in downtime, loss of productivity, and hindered business continuity.
5. Nation-State Threats: Zero-day vulnerabilities are often targeted by state-sponsored actors for intelligence gathering, cyber espionage, or sabotage purposes. These attacks can pose significant threats to national security.
Identifying and Handling Zero-Day Vulnerabilities
Given the seriousness of zero-day vulnerabilities, it is essential to have effective strategies in place to detect and handle them. Here are some practical steps to consider:
1. Stay Informed:
Keep abreast of the latest cybersecurity news, advisories, and alerts from trusted sources such as software vendors, cybersecurity organizations, and government agencies. Stay updated with information related to zero-day vulnerabilities for the software and systems you use.
2. Employ Multi-Layered Security:
Implement a multi-layered security approach that includes firewalls, intrusion detection systems, endpoint security solutions, and regular updates for operating systems and software. This approach can help mitigate the risk of zero-day attacks.
3. Practice Good Cyber Hygiene:
Adopt good cybersecurity practices such as using strong, unique passwords, enabling two-factor authentication, regularly backing up data, and avoiding suspicious email attachments or links. These practices can help minimize the impact of zero-day attacks.
4. Promptly Install Updates and Patches:
Stay vigilant about installing software updates, security patches, and firmware updates as soon as they become available. Developers often release updates in response to known vulnerabilities, including zero-day vulnerabilities.
5. Consider Security Solutions that Detect Zero-Day Attacks:
Explore advanced threat detection solutions, such as behavior-based analytics and anomaly detection, that can identify and block zero-day attacks based on their unique characteristics and patterns.
6. Conduct Regular Security Audits:
Perform comprehensive security audits on your systems, networks, and applications to identify potential vulnerabilities and address them proactively. Regular audits can help uncover zero-day vulnerabilities or indicators of compromise.
7. Engage with Security Researchers:
Establish partnerships with ethical hackers and security researchers who specialize in vulnerability discovery and disclosure. Encouraging responsible disclosure can help identify and address zero-day vulnerabilities before they are exploited.
Emerging Trends in Zero-Day Vulnerabilities
In recent times, there have been several emerging trends and challenges related to zero-day vulnerabilities:
1. Increased Demand and Value:
The demand and value for zero-day vulnerabilities have risen significantly. Nation-states, cybercriminals, and intelligence agencies are willing to pay large sums of money for exclusive access to these vulnerabilities.
2. Zero-Day Marketplaces:
The existence of underground marketplaces for buying and selling zero-day vulnerabilities has become more prevalent. These marketplaces enable anonymous transactions and create a thriving economy around zero-day exploits.
3. APT (Advanced Persistent Threat) Attacks:
Zero-day vulnerabilities are often used as part of sophisticated APT attacks. APT groups target specific organizations or individuals over an extended period, leveraging zero-day vulnerabilities to maintain persistent access and evade detection.
4. Zero-Day Exploit Kits:
Exploit kits, pre-packaged toolkits for launching cyberattacks, often include zero-day exploits. These kits make it easier for less technically skilled attackers to carry out sophisticated attacks.
5. Responsible Disclosure Initiatives:
Efforts towards responsible vulnerability disclosure have gained momentum. Software developers and security researchers are collaborating more closely to ensure vulnerabilities are reported and patched responsibly.
The Future of Zero-Day Vulnerabilities
As technology continues to evolve, so will the landscape of zero-day vulnerabilities. Here are three potential future scenarios:
1. Increased Detection and Mitigation:
The development of advanced technologies, such as artificial intelligence and machine learning, will enhance the detection and mitigation of zero-day vulnerabilities. These technologies can analyze vast amounts of data and identify potential zero-day attacks in real-time.
2. Zero-Day Exploits for IoT Devices:
As the Internet of Things (IoT) expands, the scope for zero-day vulnerabilities will likely increase. The interconnected nature of IoT devices presents new attack vectors and potential zero-day exploits that could impact various aspects of everyday life.
3. Collaboration and Cooperation:
The battle against zero-day vulnerabilities requires collaboration and cooperation among software developers, security researchers, government entities, and technology users. Increased sharing of information and joint efforts will lead to faster detection and mitigation of zero-day vulnerabilities.
In conclusion, zero-day vulnerabilities pose significant challenges in the realm of cybersecurity. Understanding the nature of these vulnerabilities and implementing proactive measures to detect and handle them is imperative. Staying informed, practicing good cyber hygiene, employing multi-layered security, and engaging with security researchers are essential steps in addressing the risks associated with zero-day vulnerabilities. By staying vigilant and adopting a holistic approach to cybersecurity, individuals and organizations can minimize the impact of these potential threats.
Key Takeaways: What Are Zero-Day Vulnerabilities, and How to Handle Them?
- Zero-day vulnerabilities are software flaws that are unknown to the software developer and can be exploited by attackers.
- These vulnerabilities pose a serious threat to computer systems and networks.
- To handle zero-day vulnerabilities, keep your software and operating systems up to date with the latest patches and updates.
- Implementing strong security measures such as firewalls and intrusion detection systems can help detect and prevent attacks.
- Regularly backing up your data and adopting secure coding practices is essential in minimizing the impact of zero-day vulnerabilities.
Frequently Asked Questions
Welcome to our FAQ section on the topic of Zero-Day Vulnerabilities and how to handle them. Here, we will address common questions about these vulnerabilities and provide insights on how to effectively manage them.
1. What is a Zero-Day Vulnerability, and why is it a concern?
A Zero-Day Vulnerability is a security flaw or weakness in software that is unknown to the vendor or software developer. It is called "Zero-Day" because the vendor has had zero days to fix or patch the vulnerability. These vulnerabilities are highly valuable to cybercriminals who exploit them to gain unauthorized access to systems, steal confidential data, or launch malicious attacks. The concerning aspect of Zero-Day Vulnerabilities is that they are not yet publicly known, which means organizations have no defense against them until a patch is released.
To protect against these vulnerabilities, it's critical to stay updated with security patches and utilize robust security measures, such as firewalls and antivirus software, to minimize the risk of exploitation.
2. How are Zero-Day Vulnerabilities discovered?
Zero-Day Vulnerabilities are discovered through multiple channels, including independent researchers, security companies, and even malicious actors. Independent researchers may identify vulnerabilities while conducting security audits or participating in bug bounty programs. Once discovered, researchers typically report the vulnerability to the software vendor to initiate remediation steps.
However, it's important to note that cybercriminals or nation-state actors may also discover Zero-Day Vulnerabilities. While some may report them to the vendor, others may use them for malicious purposes. It's crucial for organizations to have robust incident response plans in place to detect and mitigate the risks associated with Zero-Day Vulnerabilities.
3. How can organizations protect themselves against Zero-Day Vulnerabilities?
To protect against Zero-Day Vulnerabilities, organizations should implement the following measures:
First, establish a robust vulnerability management program to regularly update software and apply patches promptly. This ensures that known vulnerabilities are addressed before they can be exploited.
Second, implement strong perimeter security measures, such as firewalls and intrusion detection systems, to detect and block potential attacks targeting Zero-Day Vulnerabilities.
Third, utilize advanced threat intelligence tools and services to stay informed about emerging threats and vulnerabilities, including Zero-Days. Timely information allows organizations to proactively deploy security measures and mitigate potential risks.
Lastly, develop and practice an incident response plan that includes proactive monitoring, detection, and swift response to any potential Zero-Day Vulnerability exploits.
4. Are there any signs that indicate a system might be compromised by a Zero-Day Vulnerability?
Identifying a system compromised by a Zero-Day Vulnerability can be challenging because these vulnerabilities are unknown and leave no discernible traces. However, there are some signs organizations can look out for:
- Unusual system behavior or unexpected crashes
- Unexplained network traffic or unusual data transfers
- Unrecognized processes or services running on the system
- Unauthorized access or accounts with escalated privileges
If any of these signs are detected, it's vital to investigate further and engage an incident response team to identify the root cause and mitigate any potential damage.
5. Can antivirus software protect against Zero-Day Vulnerabilities?
While antivirus software plays a crucial role in safeguarding systems against known threats, it may not fully protect against Zero-Day Vulnerabilities. Traditional antivirus software relies on signature-based detection and may not recognize new, unknown threats without a defined signature. However, some advanced antivirus solutions utilize behavioral analysis and heuristics to detect suspicious activities that may indicate a Zero-Day Vulnerability exploit.
It's important to implement a layered approach to security, combining antivirus software with other security measures such as intrusion detection systems, strong access controls, and regular software updates. These layers of defense help minimize the risk of Zero-Day Vulnerability exploitation.
What are Zero Day Attacks?
Summary
Zero-day vulnerabilities are secret computer bugs that bad people can use to hack into systems. They're scary because there's no fix for them yet. To protect yourself, make sure to keep your software updated and use security programs.
When you hear about a zero-day attack, it means hackers found a weakness that nobody knew about. It's like a secret trapdoor they can sneak through to steal information or cause problems. So, always be cautious online and take steps to stay safe!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote