What Are The Key Components Of A Security Policy?
Welcome to the fascinating world of cybersecurity! If you've ever wondered what goes into keeping our digital world safe and secure, you've come to the right place. Today, we're diving into the topic of "What Are the Key Components of a Security Policy?" So, buckle up and get ready to uncover the secrets behind a well-rounded security strategy!
Now, you might be wondering, "Why do we even need a security policy?" Well, my curious friend, a security policy is like a set of guidelines that organizations follow to protect their valuable information and systems from potential threats. It's like having a superhero squad dedicated to defending against cyberattacks and maintaining the integrity of sensitive data.
So, what exactly are the key components of a security policy? Think of it as a recipe for a strong defense. Just like a delicious meal needs the perfect blend of ingredients, a security policy requires a combination of elements that work together to safeguard an organization's digital assets. From establishing clear rules and procedures to implementing robust technical controls, we'll explore each component in detail. Get ready to become a cybersecurity aficionado!
Are you excited to uncover the secrets behind a solid security policy? Great! In the following paragraphs, we'll explore the key components that make up this vital defense mechanism. From setting the groundwork to implementing effective controls, we'll guide you through the essential elements that form a strong security policy. So, grab your virtual magnifying glass and let's embark on this thrilling cybersecurity journey together!
Understanding the Key Components of a Security Policy
A security policy is a crucial element in ensuring the protection of an organization's assets and information. It serves as a guide for employees, outlining the necessary measures and practices to maintain a secure environment. The key components of a security policy help establish a comprehensive framework that addresses potential threats, risk management, and employee responsibilities. In this article, we will delve into the various elements that make up an effective security policy.
1. Risk Assessment
Risk assessment is the initial step in developing a security policy. It involves identifying and evaluating potential vulnerabilities and threats that may impact the organization. By conducting comprehensive risk assessments, organizations can gain insights into potential risks, prioritize their mitigation strategies, and allocate resources effectively. The process may include reviewing the physical security of premises, analyzing information security systems, and assessing external factors such as natural disasters or cyber-attacks.
An effective risk assessment should involve collaboration between departments, including the IT team, facilities management, and senior management. By identifying vulnerabilities and understanding the potential impact, organizations can develop proactive strategies to mitigate risks effectively.
2. Access Control
Access control is a vital component of any security policy. It ensures that only authorized individuals are granted access to sensitive information and critical areas within an organization. There are several aspects to consider when implementing access control measures:
- Physical Access Control: This involves securing physical spaces such as offices, data centers, and storage facilities. Measures may include the use of security personnel, access badges, surveillance systems, and biometric authentication.
- Logical Access Control: This focuses on securing digital systems and networks. It involves implementing user authentication protocols, password management policies, and role-based access control.
- Mobile Device Security: As more employees use mobile devices for work, it is crucial to establish policies and procedures to ensure their secure usage. This may include device encryption, strong authentication mechanisms, and the ability to remotely wipe data in case of loss or theft.
By implementing robust access control measures, organizations can reduce the risk of unauthorized access and protect sensitive information from falling into the wrong hands.
3. Incident Response
No organization is immune to security incidents or breaches. That is why a well-defined incident response plan is essential. An incident response plan outlines the steps to be taken in the event of a security breach, ensuring a swift and appropriate response. The key components of an incident response plan include:
- Preparation: Organizations must prepare for potential security incidents by establishing incident response teams, defining roles and responsibilities, and regularly conducting drills and training sessions.
- Detection and Analysis: Organizations need to have the necessary tools and systems in place to detect and analyze security incidents promptly. This may include intrusion detection systems, log monitoring, and threat intelligence platforms.
- Containment and Eradication: Once a security incident has been identified, it is essential to contain the impact and eliminate the root cause. This may involve isolating affected systems, patching vulnerabilities, and removing malware.
- Recovery: After containing the incident, organizations need to focus on restoring affected systems and services. Effective backup and disaster recovery strategies play a crucial role in this phase.
- Post-Incident Analysis: Conducting a thorough analysis of security incidents helps organizations identify gaps in their security measures and implement necessary improvements to prevent future breaches.
By having a well-defined incident response plan, organizations can minimize the impact of security incidents and quickly regain control of their systems.
4. Employee Awareness and Training
One of the weakest links in an organization's security posture is often its employees. Therefore, an effective security policy should include measures to raise employee awareness and provide regular training on security best practices. By educating employees about potential risks, social engineering techniques, and the importance of adhering to security policies, organizations can significantly reduce the likelihood of security incidents caused by human error.
Employee training should cover topics such as password hygiene, email phishing, safe internet browsing practices, and physical security measures. Simulated phishing exercises and periodic security awareness campaigns can reinforce the importance of security practices and remind employees to stay vigilant.
5. Compliance and Auditing
Compliance with relevant laws, regulations, and industry standards is a critical aspect of an effective security policy. Organizations must ensure that their security practices align with legal requirements and industry best practices. This may include compliance with data protection regulations, industry-specific security standards, and contractual obligations with partners and customers.
Auditing and regular security assessments play a vital role in ensuring compliance and identifying areas for improvement. Organizations should conduct internal audits or engage third-party auditors to assess their security practices, identify vulnerabilities, and verify compliance. The results of audits can inform updates and improvements to the security policy.
6. Security Awareness Programs
Security awareness programs are an essential part of any comprehensive security policy. These programs aim to educate employees about potential security risks and promote a culture of security within the organization. By conducting regular security awareness sessions, organizations can reinforce the importance of security practices, share updates on emerging threats, and encourage employees to report any suspicious activities promptly.
Effective security awareness programs may include various initiatives, such as newsletters, posters, online training modules, and interactive workshops. The goal is to create a security-conscious workforce that actively contributes to the organization's overall security posture.
7. Continuous Improvement and Evaluation
A security policy should never be static. It should be continuously evaluated and improved to adapt to evolving threats and changes within the organization. Regular evaluations help to identify gaps in security measures, assess the effectiveness of implemented controls, and make necessary adjustments.
Organizations can leverage metrics, incident reports, and feedback from employees to evaluate the success of their security policy and identify areas for improvement. By fostering a culture of continuous improvement, organizations can stay ahead of emerging threats and ensure the ongoing effectiveness of their security measures.
#Additional Content
Best Practices for Implementing a Security Policy
Now that we have explored the key components of a security policy, let's discuss some best practices for implementing and maintaining one effectively:
1. Start with a Comprehensive Risk Assessment
Conduct a thorough risk assessment to identify potential risks, prioritize them, and allocate resources accordingly. This will provide a strong foundation for developing your security policy.
2. Involve Stakeholders from Across the Organization
Ensure that representatives from different departments are involved in developing the security policy. This will help to address diverse security concerns and foster a sense of ownership.
3. Keep the Policy Simple and Easy to Understand
Avoid using unnecessary jargon or complex language in your security policy. Make it accessible to all employees by using simple terms and clear instructions.
4. Regularly Review and Update the Policy
Revisit and update the security policy periodically to incorporate emerging threats and technological advancements. Keep it relevant and aligned with current best practices.
5. Provide Ongoing Training and Education
Continuous training and education are essential to ensure that employees stay up-to-date with security best practices and understand their role in safeguarding the organization's assets.
6. Foster a Culture of Security
Make security a shared responsibility and encourage employees to report any security concerns or incidents promptly. Reward and recognize employees who actively contribute to the organization's security.
7. Regularly Test and Assess Security Measures
Conduct periodic security assessments, penetration tests, and simulations to identify vulnerabilities and validate the effectiveness of implemented controls. Use the results to make informed improvements.
In conclusion, a security policy is a crucial component for organizations aiming to protect their assets and information. By incorporating comprehensive risk assessments, effective access control measures, incident response plans, employee awareness programs, and ongoing evaluation, organizations can create a robust security framework. Regular updates, employee training, and external audits ensure compliance and continuous improvement. Implementing a security policy requires a holistic approach that involves all stakeholders and fosters a culture of security awareness.
Key Takeaways: "What Are the Key Components of a Security Policy?"
- A security policy outlines guidelines and procedures for protecting sensitive data and information.
- It includes access control measures to ensure only authorized individuals can access resources.
- A security policy also addresses data encryption and secure communication protocols.
- Regular security audits and monitoring are essential components of a security policy.
- Employee awareness and training play a crucial role in implementing a security policy effectively.
Frequently Asked Questions
A security policy is a crucial aspect of any organization's cybersecurity strategy. It sets guidelines and procedures to protect sensitive information, systems, and networks. Here are some common questions about the key components of a security policy.
1. Why is it important to have a security policy?
A security policy serves as a roadmap for protecting an organization's assets from potential threats. It provides clear guidelines on how to handle and secure sensitive information, helps prevent unauthorized access, and ensures compliance with industry regulations. By having a security policy in place, organizations can proactively address security risks and minimize the impact of potential cyber attacks.
Furthermore, a security policy helps create awareness among employees regarding their responsibilities in maintaining data security. It establishes a culture of cybersecurity within the organization and fosters a sense of trust with customers and partners who rely on the protection of their information.
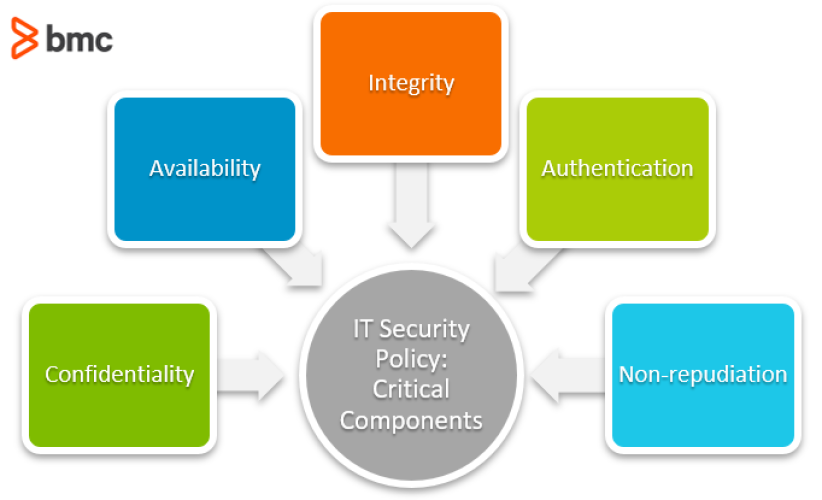
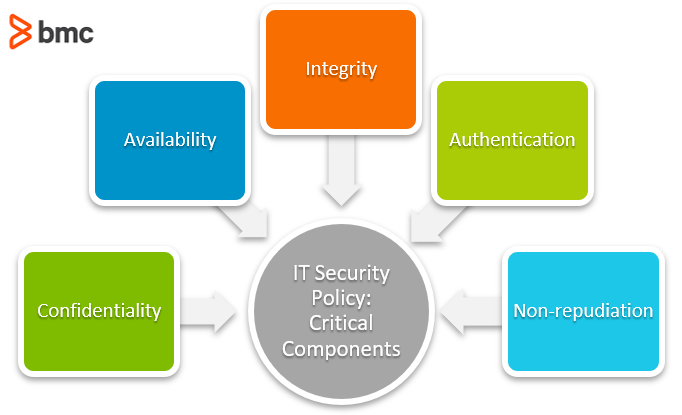
2. What are the main components of a security policy?
A security policy typically consists of several key components. These may include:
1. Statement of intent: This section describes the purpose and objectives of the security policy, outlining the organization's commitment to safeguarding its data and systems.
2. Scope: The scope defines the systems, networks, and assets covered by the security policy. It clarifies the boundaries within which the policy applies, ensuring comprehensive coverage without being overly broad.
3. Roles and responsibilities: This component delineates the responsibilities of individuals within the organization concerning security, such as management, IT staff, and end-users. It ensures that everyone understands their role in maintaining a secure environment.
4. Access control: This section outlines the rules and procedures for granting access to resources. It includes guidelines for user authentication, password management, and data classification, ensuring that only authorized individuals can access sensitive information.
5. Incident response plan: A security policy should also include a well-defined plan for handling security incidents. This plan outlines the necessary steps to be taken in the event of a data breach, cyber attack, or other security incidents, ensuring a swift and effective response.
3. How should a security policy be communicated to employees?
Communicating the security policy effectively to employees is vital to ensure understanding and compliance. Here are some best practices:
1. Clear documentation: The security policy should be documented in a clear and concise manner, avoiding unnecessary technical jargon. It should be easily accessible to all employees through the company intranet or shared drives.
2. Training and awareness programs: Conduct regular training sessions and awareness programs to educate employees about the security policy. These sessions can cover best practices, procedures, and potential risks to enhance employees' understanding of their role in maintaining security.
3. Acknowledgement and consent: Require employees to sign an acknowledgement form stating that they have read, understood, and will adhere to the security policy. This helps create a sense of responsibility and accountability among employees.
4. Ongoing reminders and updates: Reinforce the security policy through periodic reminders, newsletters, or internal communication channels. Highlight any updates or changes to the policy to keep employees informed and ensure compliance with the latest guidelines.
4. How often should a security policy be reviewed and updated?
A security policy should be reviewed and updated regularly to adapt to the evolving threat landscape. The frequency of reviews may vary depending on factors such as industry regulations and the organization's risk appetite, but generally, it is recommended to review the policy annually or when significant changes occur.
Regular reviews help identify any gaps or weaknesses in the policy and ensure its alignment with current best practices and compliance requirements. It is essential to involve relevant stakeholders, such as IT personnel and management, in the review process to gather valuable input and insights.
5. How can a security policy be enforced effectively?
Enforcing a security policy requires a combination of technical measures, training, and clear communication. Here are some strategies:
1. Access controls: Implement robust access controls, including user authentication, strong passwords, and encryption, to restrict unauthorized access to sensitive data and systems.
2. Monitoring and auditing: Regularly monitor system logs and conduct audits to identify any irregularities or deviations from the security policy. This helps ensure that employees are adhering to the established guidelines.
3. Incident response protocols: Establish clear incident response protocols and workflows to address security incidents promptly and effectively. This includes assigning responsibilities, defining escalation paths, and conducting post-incident analysis to learn from any breaches or attacks.
4. Continuous training and awareness: Keep employees informed about the latest security threats, trends, and best practices through ongoing training and awareness programs. This helps reinforce the importance of following the security policy and prepares employees to recognize and respond to potential security risks effectively.
5. Regular evaluations and updates: Continuously evaluate the effectiveness of the security policy and make necessary updates based on emerging threats, technological advancements, and industry standards. Staying current ensures that the policy remains robust and relevant in addressing new security challenges.
IT Security Policy: Key Components
Summary:
Setting up a security policy is important to keep things safe and secure. It helps protect valuable information and keeps bad guys out. A good security policy has three main parts: rules, roles, and tools. Rules tell people what they can and can't do to keep things secure. Roles make sure the right people have the right access to information. Tools are like locks on doors and firewalls that stop bad guys from getting in. So remember, a security policy is like a superhero cape that keeps things safe and protects against bad guys!
In conclusion, a security policy is like a superhero cape, with rules, roles, and tools working together to protect valuable information from the bad guys. It's a way to make sure everyone knows how to keep things safe and secure. So next time, don't forget to put on your security cape and keep the world safe!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote