What Are The Basics Of Data Encryption?
In the world of technology and digital communication, data encryption plays a vital role in protecting our sensitive information. So, what are the basics of data encryption? Let's uncover the fascinating world of safeguarding data together.
Data encryption is like a secret code that keeps our information safe from prying eyes. It's like putting your words in a locked box, where only those with the right key can unlock it.
Imagine you're sending a message to your best friend. With encryption, your message goes through a magical process that scrambles it into a jumble of characters. Only your friend, who has the key, can unscramble and read your message. That's the power of data encryption!
Are you ready to dive deeper into the fascinating world of data encryption? Let's explore how it works, the different encryption methods, and why it is so important in today's digital age. Together, we'll unlock the secrets of keeping our data secure.
Understanding the Basics of Data Encryption: A Beginner's Guide
Data encryption is a critical component of modern cybersecurity. In an era where digital information is constantly under threat, it is crucial to understand the basics of data encryption to protect sensitive data from unauthorized access. This article aims to demystify data encryption and provide a comprehensive guide for beginners. Whether you're a curious individual or an aspiring cybersecurity professional, this article will equip you with the knowledge needed to navigate the complex world of encryption.
Why Is Data Encryption Important?
Data encryption plays a vital role in securing confidential information from prying eyes, both during storage and transmission. By converting data into an unreadable format, encryption ensures that even if it falls into the wrong hands, it remains unintelligible and unusable. This protects sensitive data such as personal information, financial records, and intellectual property. The importance of data encryption extends to safeguarding national security secrets and preventing cybercriminals from exploiting vulnerabilities for malicious purposes.
The Science Behind Data Encryption
To understand how data encryption works, we need to delve into the science behind it. At its core, encryption relies on cryptographic algorithms that utilize mathematical functions to transform plain text into ciphertext. There are two main types of encryption: symmetric encryption and asymmetric encryption.
Symmetric Encryption
Symmetric encryption, also known as secret-key encryption, involves the use of a single key for both encryption and decryption. The sender and the recipient share the same key, which must be kept secret. This key is used to convert the plain text into ciphertext and vice versa. Symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are highly efficient and widely used, making them suitable for encrypting large amounts of data.
However, the main challenge with symmetric encryption lies in securely exchanging the key between the sender and the recipient. If the key is intercepted by an attacker, they can easily decrypt the ciphertext. This vulnerability led to the development of asymmetric encryption.
Asymmetric Encryption
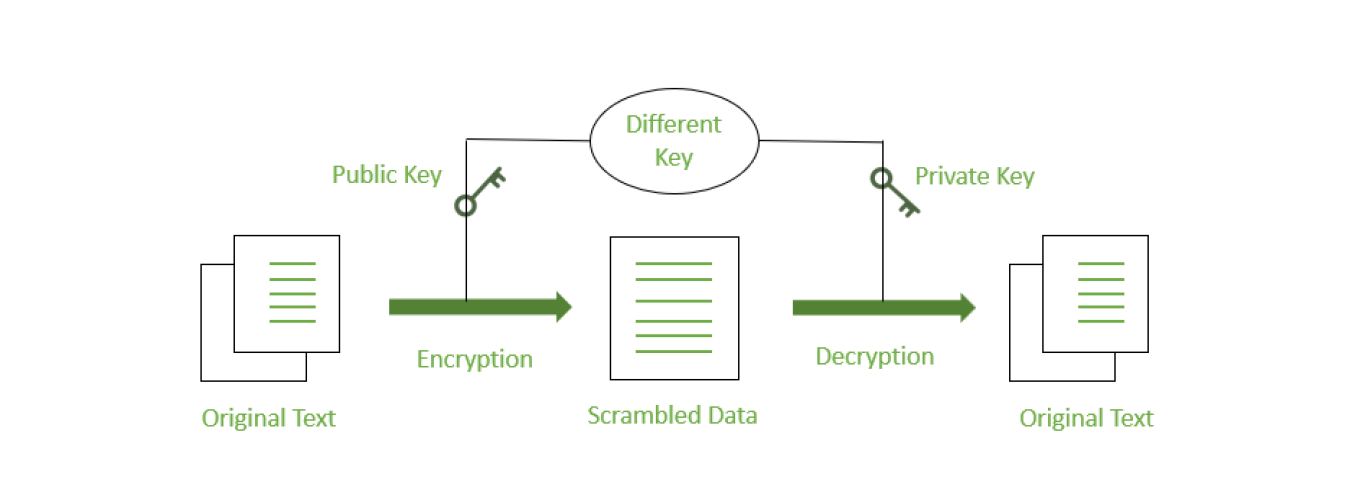
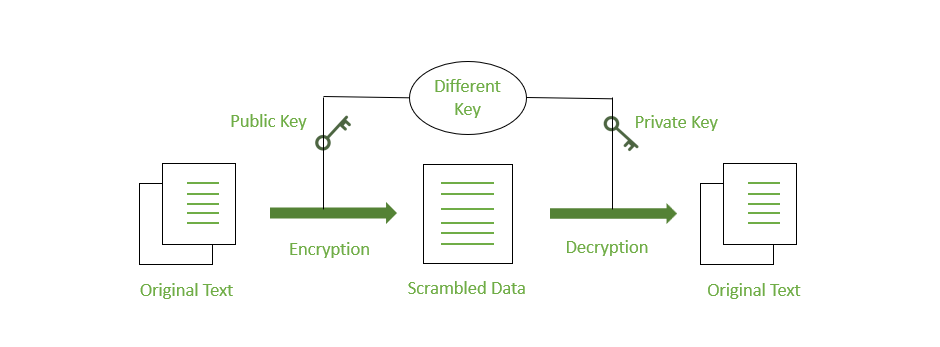
Asymmetric encryption, also known as public-key encryption, utilizes a pair of keys: a public key and a private key. The public key is freely shared, while the private key is kept confidential. Anything encrypted with the public key can only be decrypted with the corresponding private key, ensuring that only the intended recipient can access the decrypted message.
Asymmetric encryption solves the key exchange problem present in symmetric encryption. However, it is computationally more expensive and slower than symmetric encryption. Therefore, a hybrid approach is often used, where data is encrypted symmetrically using a randomly generated key, and then this key is encrypted asymmetrically using the recipient's public key. This ensures both efficiency and security.
The Role of Encryption Keys
In both symmetric and asymmetric encryption, encryption keys are vital components. Encryption keys are essentially a sequence of bits that determine how the encryption algorithm transforms data. For symmetric encryption, the same key is used for both encryption and decryption, while for asymmetric encryption, a pair of mathematically related keys is used. The longer and more complex the encryption key, the more secure the encryption.
Encryption keys should be kept confidential and securely managed. The loss of an encryption key can result in permanent data loss, as encrypted data cannot be decrypted without the corresponding key. It is also crucial to regularly update encryption keys to maintain security and mitigate the risk of key compromise.
Real-World Applications of Data Encryption
Data encryption is widely used in various sectors to protect sensitive information. Some common applications include:
- Secure Communication: Encryption ensures the confidentiality of emails, instant messages, and sensitive online communications, guarding against eavesdropping and unauthorized access.
- E-commerce: Encryption protects customers' financial data during online transactions, preventing unauthorized access to credit card information and personal details.
- Healthcare: Encryption safeguards patients' medical records and personal health information, ensuring compliance with privacy regulations such as the Health Insurance Portability and Accountability Act (HIPAA).
- Government and Defense: Encryption is used to secure classified information, intelligence reports, military communications, and diplomatic correspondence, protecting national security interests.
Understanding the basics of data encryption is essential in today's digital age. Whether you're an individual seeking to protect personal information or an organization concerned with data security, encryption is a fundamental tool to safeguard sensitive data. By implementing robust encryption protocols and best practices, individuals and businesses can mitigate the risk of data breaches and unauthorized access.
Choosing the Right Encryption Algorithm
When it comes to data encryption, choosing the right encryption algorithm is crucial to ensure the security of your data. Different encryption algorithms offer varying levels of strength, efficiency, and suitability for different applications. Here are three popular encryption algorithms:
Advanced Encryption Standard (AES)
The Advanced Encryption Standard (AES) is one of the most widely used symmetric encryption algorithms. Adopted by the U.S. government and used extensively worldwide, AES offers a high level of security and efficiency. It operates on fixed block sizes of data and supports key lengths of 128, 192, and 256 bits. AES has become the standard for encrypting sensitive data in various fields, including finance, healthcare, and government.
One of the advantages of AES is its resistance to brute-force attacks. The computational power required to break AES encryption by testing all possible keys is currently infeasible. However, it is important to ensure that the encryption key used with AES is sufficiently strong and securely managed.
Rivest-Shamir-Adleman (RSA)
RSA is an asymmetric encryption algorithm widely used for tasks such as securing online communication, digital signatures, and key exchange. Named after its creators, RSA utilizes the mathematical properties of large prime numbers and modular arithmetic. RSA encryption is based on the fact that it is computationally difficult to factorize large numbers into their prime factors.
One of the key advantages of RSA is its key exchange capabilities. The public and private keys used in RSA allow secure communication even when parties have not previously shared any secrets. RSA is often used in combination with symmetric encryption algorithms for secure communication over public networks.
Elliptic Curve Cryptography (ECC)
Elliptic Curve Cryptography (ECC) is a family of public-key algorithms that offer strong security with shorter key lengths compared to traditional asymmetric algorithms such as RSA. ECC is based on the mathematical properties of elliptic curves over finite fields. This makes ECC particularly suitable for low-power devices and environments where bandwidth is limited.
ECC has gained popularity in recent years for applications that demand efficiency and security, such as mobile devices, Internet of Things (IoT) devices, and wireless communication. ECC offers the same level of security as traditional asymmetric algorithms, but with shorter keys, reducing computational overhead and improving performance.
Best Practices for Data Encryption
Data encryption is only effective when implemented correctly. To ensure the security of your data, it is essential to follow best practices in encryption. Here are some key tips:
1. Use Strong Encryption Algorithms
Always select encryption algorithms that offer strong security. Choose algorithms such as AES, RSA, or ECC, which are widely recognized and have undergone extensive scrutiny by the security community. Avoid using obsolete or insecure encryption algorithms that can be easily cracked.
Benefit:
Using strong encryption algorithms ensures that your data remains safe from unauthorized access. By leveraging the security provided by established encryption algorithms, you can protect your valuable information from cyber threats.
Tip:
Regularly update your encryption algorithms to ensure that you are using the latest and most secure versions. As new vulnerabilities are discovered, encryption algorithms may be updated to address these issues and provide enhanced security.
Example:
For example, if you are using symmetric encryption, consider upgrading to AES-256 from an earlier version such as AES-128. AES-256 offers a higher level of security by using a longer key length, making it more resistant to brute-force attacks.
2. Generate Strong Encryption Keys
Encryption keys are the cornerstone of data encryption. It is essential to generate strong, random encryption keys that are resistant to guessing or brute-force attacks. Avoid using easily guessable or predictable keys, such as common phrases, personal information, or sequential numbers.
Benefit:
Generating strong encryption keys ensures that even if an attacker gains access to your encrypted data, they will not be able to decrypt it without the corresponding key. Strong encryption keys add an additional layer of protection to your data.
Tip:
Use cryptographically secure random number generators to generate encryption keys. These generators provide true randomness and ensure that keys are not biased or guessable. Additionally, consider using key management systems to securely store and manage your encryption keys.
Example:
Instead of using a commonly used password as your encryption key, generate a random key consisting of a combination of uppercase and lowercase letters, numbers, and special characters. This significantly increases the complexity of the key and enhances security.
3. Implement Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your encryption mechanisms. By requiring an additional authentication factor, such as a one-time password or biometric data, alongside the encryption key, you can prevent unauthorized access even if the key is compromised.
Benefit:
Implementing two-factor authentication reduces the risk of unauthorized access to encrypted data. It ensures that an attacker cannot decrypt the data solely with the encryption key, adding an additional barrier to protect sensitive information.
Tip:
Whenever possible, consider using multi-factor authentication (MFA) instead of two-factor authentication. MFA requires the user to provide multiple independent authentication factors, such as a password, a fingerprint scan, and a security token. This further enhances the security of encrypted data.
Example:
If you are encrypting files on a computer or a cloud storage platform, enable two-factor authentication for accessing those files. This will require the user to provide a second form of authentication, such as a fingerprint scan or a verification code delivered to their phone, in addition to the encryption key.
4. Regularly Update and Patch Your Software
Regular software updates and patches are crucial for maintaining the security of your encryption systems. Software vulnerabilities can be exploited by attackers to gain unauthorized access to encrypted data. By promptly applying updates and patches, you can ensure that any vulnerabilities are addressed and security is strengthened.
Benefit:
Updating and patching your software minimizes the risk of security breaches due to known vulnerabilities. It ensures that your encryption systems are up to date and capable of defending against the latest threats.
Tip:
Regularly check for updates from the software vendors or developers of your encryption tools. Enable automatic updates whenever possible to ensure that you receive the latest security patches without delay. Additionally, regularly monitor security news and advisories to stay informed about potential vulnerabilities.
Example:
If you are using an encryption software or a security tool, always keep it up to date by downloading the latest version from the official website or using the built-in update option within the software.
The Bottom Line
Data encryption is a fundamental aspect of modern cybersecurity. Understanding the basics of data encryption, including encryption algorithms, encryption keys, and best practices, is essential for anyone concerned about the security of sensitive information. By implementing strong encryption measures and following best practices, individuals and organizations can safeguard their data from unauthorized access and mitigate the risks associated with data breaches. Remember, encryption is a powerful tool, but it is not a standalone solution. It should be used in conjunction with other layers of security to establish a robust defense against cyber threats.
Key Takeaways: What Are the Basics of Data Encryption?
- Data encryption is a method used to protect sensitive information by converting it into an unreadable format.
- Encryption relies on algorithms and keys to encrypt and decrypt data.
- The two main types of encryption are symmetric encryption and asymmetric encryption.
- Common encryption algorithms include AES, RSA, and DES.
- Data encryption is important for ensuring the confidentiality and integrity of data.
Frequently Asked Questions
Welcome to our FAQ section! Here, we'll explore the basics of data encryption, a crucial aspect of protecting sensitive information. Read on to find answers to commonly asked questions about data encryption.
Q: Why is data encryption important?
Data encryption is essential because it provides a layer of security that helps safeguard sensitive information from unauthorized access. By converting data into a code that can only be deciphered with the appropriate decryption key, encryption ensures that even if data is intercepted, it remains incomprehensible to unauthorized individuals.
Encryption is particularly crucial in the digital world, where cyber threats are prevalent. Whether it's personal data, financial information, or sensitive business data, encryption helps protect against data breaches, identity theft, and unauthorized tampering.
Q: How does data encryption work?
Data encryption works by transforming plain text or data into an unreadable format through complex mathematical algorithms. This process involves an encryption algorithm and a key. The algorithm is a set of instructions that define how the data is transformed, while the key is a unique code that enables the conversion to occur.
When data is encrypted, it becomes ciphertext- a jumble of characters that can only be deciphered using the corresponding decryption key. This creates a secure method of storing or transmitting sensitive information, as only those with the correct decryption key can unlock and interpret the data.
Q: What are some common encryption algorithms?
There are various encryption algorithms used to secure data. Some of the most common ones include:
- Advanced Encryption Standard (AES): A widely used symmetric encryption algorithm known for its high levels of security.
- RSA: An asymmetric encryption algorithm that employs both a public key for encryption and a private key for decryption.
- Triple Data Encryption Standard (3DES): A symmetric encryption algorithm that applies the Data Encryption Standard (DES) algorithm multiple times for enhanced security.
- Blowfish: A symmetric key block cipher that can be useful for applications requiring fast encryption and decryption.
Each algorithm has its own strengths and weaknesses, and the choice of algorithm depends on the specific use case and security requirements.
Q: Can encrypted data be decrypted?
Encrypted data can be decrypted, but only by those who possess the correct decryption key. The purpose of encryption is to ensure that unauthorized individuals cannot easily decipher the encrypted data without the key.
However, it is worth noting that with advancements in technology, malicious actors are constantly attempting to break encryption algorithms. It is crucial to use strong encryption methods and regularly update encryption practices to stay ahead of potential threats.
Q: Is data encryption only for cybersecurity professionals?
No, data encryption is not limited to cybersecurity professionals. In fact, anyone who handles sensitive information, whether on a personal or professional level, can benefit from understanding and implementing data encryption practices.
Individuals can take steps like using encrypted messaging apps, enabling encryption on their devices, and ensuring secure internet connections to protect their own data. Similarly, businesses of all sizes should prioritize encryption to safeguard customer data, financial information, and trade secrets from data breaches and cyber attacks.
Encryption Explained Simply | What Is Encryption? | Cryptography And Network Security | Simplilearn
Summary
Data encryption is like putting a secret code on your messages or files. It takes your information and turns it into a jumbled mess that only someone with the secret code can understand. Encryption uses special algorithms, or rules, to scramble and unscramble the data. This keeps your sensitive information safe from prying eyes and hackers. There are two main types of encryption: symmetric and asymmetric. Symmetric encryption uses one secret key, while asymmetric encryption uses a pair of keys, one for locking and one for unlocking the data. It's important to use strong encryption methods to protect your data and keep it secure.
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote