How To Secure IoT Devices In The Workplace?
In today's world, technology plays a vital role in our everyday lives. From smartphones to smart homes, it seems like everything is connected. And in the workplace, this connectivity extends to IoT devices. But how do we ensure the security of these devices? Well, that's exactly what we're going to explore in this article on "How to Secure IoT Devices in the Workplace?"
As technology advances, so do the threats that come along with it. With IoT devices becoming more prevalent in offices and workplaces, it's crucial to take steps to protect sensitive information and maintain a secure environment. In this guide, we'll walk you through the best practices and actionable tips to safeguard your IoT devices and keep potential vulnerabilities at bay.
So, whether you're an employee seeking to enhance the security of your workplace or a business owner looking to fortify your IoT infrastructure, grab a seat and get ready to learn the essential steps to secure IoT devices in the workplace. Let's dive in!
- 1. Assess the IoT devices: Identify all the devices connected to the network.
- 2. Strengthen network security: Update passwords, enable two-factor authentication, and firewall protection.
- 3. Regularly update software: Keep all IoT devices updated with the latest security patches.
- 4. Control access rights: Grant access only to authorized personnel and regularly review user privileges.
- 5. Educate employees: Train staff on IoT security best practices to prevent potential breaches.

How to Secure IoT Devices in the Workplace: Safeguarding Your Business and Data
The increasing adoption of Internet of Things (IoT) devices in the workplace brings immense benefits, but it also poses significant security risks. From connected printers and smart thermostats to surveillance cameras and wearable devices, IoT devices are transforming the way businesses operate. However, their connectivity and vulnerabilities make them attractive targets for cybercriminals. To ensure the safety of your organization's sensitive data and protect against potential threats, it is crucial to implement robust security measures for IoT devices in the workplace. In this article, we will explore seven essential steps to help you secure these devices effectively.
1. Conduct a Comprehensive Inventory of IoT Devices
Before you can secure your IoT devices, you need to know what you have. Begin by conducting an inventory of all the IoT devices in your workplace. This includes everything from smart thermostats and connected printers to security cameras and wearable devices. Take note of the make, model, and operating system of each device, as well as their purpose and location. This information will be invaluable as you develop your security strategy.
Once you have a complete inventory, it is essential to keep it updated. New IoT devices are continuously being introduced, and existing devices may be replaced or decommissioned. Regularly review and update your inventory to reflect any changes in your workplace's IoT landscape.
Consider the following when conducting an inventory:
1. Document the make, model, and operating system of each IoT device.
2. Include information on the purpose and location of each device.
3. Continuously update the inventory as new devices are introduced or retired.
2. Implement Strong Authentication Measures
To protect against unauthorized access, it is crucial to implement strong authentication measures for your IoT devices. Weak or default passwords are one of the most common vulnerabilities in IoT security. Change all default passwords immediately upon installation, and create strong, unique passwords for each device.
Consider implementing two-factor authentication (2FA) for your IoT devices. With 2FA, users must provide two forms of identification to access the device—typically a password and a unique code sent to their mobile device. This adds an extra layer of security and significantly reduces the risk of unauthorized access.
Follow these best practices for implementing strong authentication:
1. Change default passwords immediately upon installation.
2. Create strong, unique passwords for each IoT device.
3. Implement two-factor authentication (2FA) for added security.
3. Segment Your Network
Segmenting your network is an essential step in securing IoT devices. By separating your IoT devices from your main network, you can isolate potential threats and limit the impact of a breach. Create a dedicated network specifically for your IoT devices and implement access control measures to restrict communication with the rest of your network.
When segmenting your network, consider the different types of devices you have and their security requirements. For example, high-risk devices such as surveillance cameras should be kept separate from mission-critical systems to minimize the risk of unauthorized access or data breaches.
Best practices for segmenting your network:
1. Create a dedicated network for IoT devices.
2. Implement access control measures to restrict communication with the main network.
3. Separate high-risk devices from mission-critical systems for added security.
4. Regularly Update and Patch IoT Devices
Keeping your IoT devices up to date with the latest firmware and security patches is crucial to maintain their security. Manufacturers often release updates that address known vulnerabilities and enhance device security. Regularly check for updates and patches for all your IoT devices and apply them promptly.
In addition to firmware updates, also ensure that any companion applications or management software used to control the IoT devices are kept up to date. These applications may contain vulnerabilities that can be exploited by cybercriminals.
Follow these guidelines for keeping your IoT devices updated:
1. Regularly check for firmware updates and security patches.
2. Apply updates promptly to address known vulnerabilities.
3. Keep companion applications and management software up to date.
5. Encrypt Data in Transit and at Rest
Encrypting data is essential to protect it from unauthorized access and interception. When transmitting data between IoT devices and other systems, ensure that it is encrypted using secure protocols, such as Transport Layer Security (TLS). This prevents attackers from eavesdropping on the communication and stealing sensitive information.
Similarly, data at rest on the IoT devices themselves should also be encrypted. In the event of physical device theft or unauthorized access, encryption ensures that the data remains unintelligible and unusable.
Best practices for encrypting data in transit and at rest:
1. Use secure protocols like TLS to encrypt data in transit.
2. Encrypt data stored on IoT devices to protect against physical theft or unauthorized access.
6. Monitor and Analyze IoT Device Activity
Effective monitoring and analysis of IoT device activity can help you detect potential security threats and anomalies. Implement a robust IoT device monitoring system that tracks device behavior, network traffic, and data transfers. This allows you to identify any suspicious activity and respond promptly to potential threats.
Leverage machine learning and artificial intelligence (AI) technologies to analyze IoT device data and proactively detect anomalies or patterns indicative of a security breach. By continuously monitoring and analyzing device activity, you can stay one step ahead of potential attackers.
Best practices for monitoring and analyzing IoT device activity:
1. Implement a robust IoT device monitoring system.
2. Track device behavior, network traffic, and data transfers.
3. Leverage machine learning and AI technologies to detect anomalies and potential threats.
7. Educate Employees on IoT Security Best Practices
Your employees play a crucial role in securing IoT devices in the workplace. Educate them about the risks associated with IoT devices and the role they play in maintaining security. Provide training on IoT security best practices, including strong passwords, phishing awareness, and proper handling of IoT devices.
Encourage employees to report any suspicious activity or potential security breaches immediately. Foster a culture of cybersecurity awareness and make it clear that maintaining the security of IoT devices is a shared responsibility.
Important points to cover in employee education on IoT security:
1. Explain the risks associated with IoT devices.
2. Provide training on strong passwords and phishing awareness.
3. Encourage employees to report suspicious activity promptly.
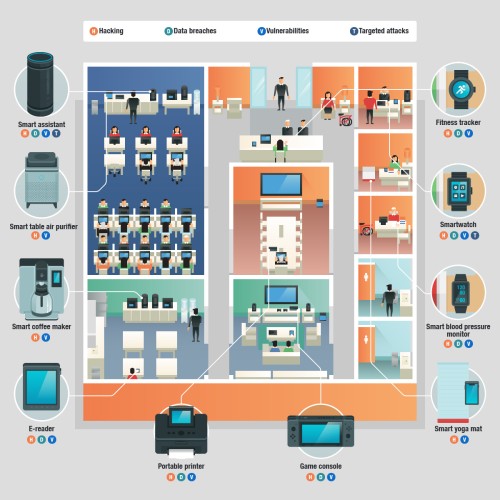
Common IoT Devices and Their Security Risks
Protecting IoT Devices from Malware and Cyberattacks
Implementing Security Policies and Compliance for IoT Devices in the Workplace
In Summary,
Securing IoT devices in the workplace is paramount to protect your business and data from cybersecurity threats. By conducting a comprehensive inventory, implementing strong authentication measures, segmenting your network, regularly updating and patching devices, encrypting data, monitoring and analyzing device activity, and educating employees, you can significantly enhance the security of your IoT ecosystem. Stay vigilant, maintain best practices, and adapt to emerging threats to ensure your organization remains protected in the fast-evolving landscape of IoT security.
Key Takeaways: How to Secure IoT Devices in the Workplace?
- Use strong and unique passwords for IoT devices.
- Regularly update firmware and software to patch vulnerabilities.
- Implement network segmentation to isolate IoT devices from critical systems.
- Enable two-factor authentication for added security.
- Train employees on recognizing and avoiding phishing attacks.
Frequently Asked Questions
In today's workplace, Internet of Things (IoT) devices are becoming increasingly common. However, with the rise in connectivity comes the need for robust security measures. To keep your IoT devices secure in the workplace, here are some commonly asked questions and their answers:
1. How can I ensure the security of IoT devices in my workplace?
To secure IoT devices in the workplace, it is crucial to follow a few key steps. Firstly, always change the default usernames and passwords on IoT devices. This simple measure can prevent unauthorized access. Additionally, ensure that all IoT devices are regularly updated with the latest firmware and security patches. This helps address any vulnerabilities that may exist.
Another essential measure is to segment your network. By separating IoT devices from other critical business systems, you create an extra layer of protection. Implementing strong encryption protocols, such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS), further enhances security. Finally, educate your employees about the importance of IoT security and train them on how to identify and report any suspicious activity.
2. Can I use the same security measures for all types of IoT devices?
While there are universal security practices, different IoT devices may require specific measures. The security measures for a smart thermostat, for example, might differ from those needed for a security camera. It is essential to review the manufacturer's guidelines for each IoT device to identify the specific security protocols they recommend.
Furthermore, some IoT devices have limited processing power and memory, making traditional security measures impractical. In such cases, implementing network security measures, such as firewalls and intrusion detection systems, can provide an additional layer of protection for these devices.
3. What are the risks of not securing IoT devices in the workplace?
The risks of leaving IoT devices unsecured can be significant. Hackers can exploit vulnerabilities in IoT devices to gain unauthorized access to your network or steal sensitive information. Unsecured IoT devices can also become targets for botnets, which can be used to launch large-scale cyber attacks.
In addition to compromising data security, unsecured IoT devices can impact the functioning of your network. Malicious actors may gain control over IoT devices, disrupting operations or causing downtime. This can result in financial losses, damage to your reputation, and potential legal consequences.
4. How can I monitor and detect unauthorized access to IoT devices?
To monitor and detect unauthorized access to IoT devices, you can utilize network monitoring tools. These tools allow you to monitor the traffic between IoT devices and your network, flagging any unusual or suspicious activity. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can also help identify and prevent unauthorized access.
Regularly reviewing logs and conducting security audits can provide further insights into potential security breaches. Implementing strong authentication mechanisms, such as two-factor authentication, can add an extra layer of security by requiring users to provide additional verification before accessing IoT devices.
5. Are there any privacy concerns associated with IoT devices in the workplace?
Yes, there are privacy concerns associated with IoT devices in the workplace. IoT devices collect and transmit various types of data, including personal and sensitive information. If not properly secured, this data can be intercepted and exploited by cybercriminals.
Employers should be transparent with their employees about the types of data collected and how it will be used. Implementing privacy policies, obtaining consent for data collection, and storing collected data securely are essential steps to address privacy concerns. Regularly reviewing and updating privacy practices ensures compliance with data protection regulations and safeguards employee privacy.
Summary
Here's what you need to know about securing IoT devices in the workplace:
First, make sure to change default passwords to strong ones that are hard to guess.
Second, keep your devices up to date with the latest software and firmware updates.
And finally, create a separate network for IoT devices to isolate them from sensitive data.
By following these steps, you can help protect your workplace from IoT security risks. Stay safe!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote