How To Respond To A Security Incident Effectively?
Are you wondering how to respond to a security incident effectively? In today's digital world, it's crucial to be prepared for potential threats and know how to handle them. So, let's dive into some practical tips that will help you respond to a security incident like a pro.
Picture this: You're sitting at your computer, engrossed in an online game or chatting with friends when suddenly, a message pops up warning of a potential security breach. What do you do? Don't panic! With the right knowledge and steps, you can handle the situation calmly and effectively.
In this article, we'll walk through the essential steps to respond to a security incident, from identifying the issue to mitigating its impact. Let's explore how you can protect yourself, your data, and your digital world when faced with a security incident. So, buckle up and get ready to become a cybersecurity superhero!
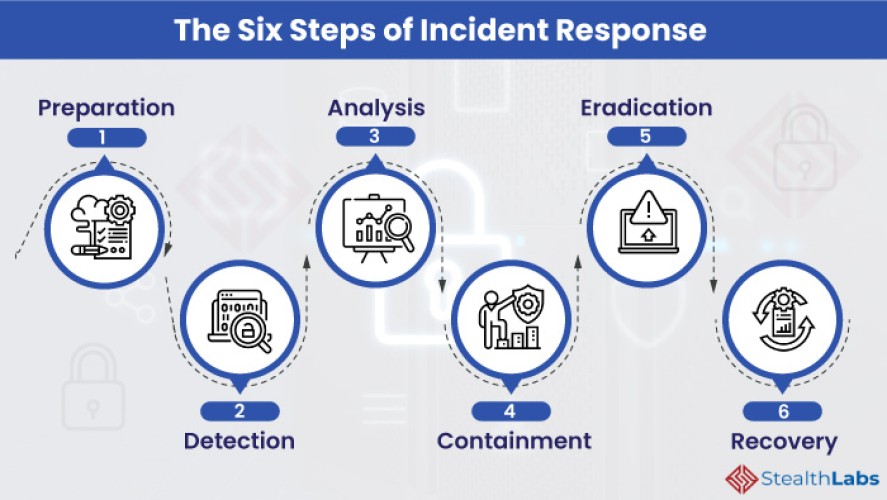
- Assess the Situation: Determine the nature and extent of the incident.
- Contain the Incident: Isolate affected systems to prevent further damage.
- Investigate and Identify: Gather evidence and analyze the cause of the incident.
- Notify Relevant Parties: Inform internal stakeholders and authorities as necessary.
- Recover and Learn: Restore systems, review the incident, and implement preventive measures.
Remember, when responding to a security incident effectively, these step-by-step actions can help minimize the impact, protect data, and prevent future breaches.

How to Respond to a Security Incident Effectively?
When it comes to cybersecurity, preparation is key. However, even the most secure systems can fall victim to a security incident. In such cases, a quick and effective response is crucial to minimize damage and prevent further breaches. In this article, we will explore the best practices for responding to a security incident, from identifying the incident to implementing remediation measures. Whether you are an individual or an organization, understanding these steps will help you effectively manage and mitigate the impact of a security incident.
Step 1: Identify and Assess the Incident
The first step in responding to a security incident is to identify and assess the situation. This involves being vigilant and proactive in detecting any signs of a breach. Look out for unusual activities, such as unauthorized access attempts, abnormal system behavior, or suspicious network traffic. It is important to have monitoring systems in place that can alert you to potential incidents. Once an incident is detected, gather as much information as possible about the event. This includes documenting the date and time of the incident, the systems or assets affected, and any evidence that can help in the investigation.
Next, it is crucial to assess the severity and impact of the incident. Consider the potential harm that could result from the breach, such as data leaks, financial loss, reputation damage, or legal implications. This will help determine the level of urgency and resources needed to respond effectively. It is also important to consider any regulatory or compliance requirements that may be applicable to your industry, as this can affect the steps you need to take in the aftermath of a security incident.
Step 2: Contain the Incident and Limit Further Damage
After identifying and assessing the incident, the next step is to contain the breach and limit further damage. This involves isolating the affected systems or assets to prevent the incident from spreading. Disconnect compromised devices from the network and disable any user accounts or access points associated with the incident. Implementing temporary security measures, such as firewalls or intrusion prevention systems, can help prevent additional unauthorized access.
Once the incident is contained, it is essential to preserve any evidence related to the breach. This includes system logs, network traffic captures, and any other relevant data that can aid in the investigation. Taking snapshots or forensic images of affected systems can also be valuable for forensic analysis. By preserving evidence, you will be better equipped to determine the root cause of the incident and prevent future breaches.
Step 3: Investigate and Remediate
After securing the breached systems, the next step is to investigate the incident and determine the root cause. This involves conducting a thorough analysis of the compromised systems, examining logs and files, and interviewing relevant personnel. Engaging with cybersecurity experts or incident response teams can provide valuable insights and expertise during this phase.
Based on the findings of the investigation, develop a remediation plan to address the vulnerabilities that led to the security incident. This may involve patching or updating software, strengthening access controls, enhancing network security, or conducting employee training on cybersecurity best practices. It is important to prioritize these actions based on the severity and impact of the incident.
Regularly reviewing and updating your incident response plan is also essential. This ensures that your organization remains prepared to handle future security incidents effectively. Conduct post-incident reviews to identify areas where improvements can be made and incorporate any lessons learned into your incident response strategy.
Key Takeaways: How to Respond to a Security Incident Effectively?
- Act immediately: As soon as you discover a security incident, take prompt action to address and contain the issue.
- Notify relevant authorities: Inform the necessary parties, such as law enforcement or your organization's IT department, about the incident.
- Gather evidence: Document and collect all relevant information and evidence pertaining to the security incident.
- Communicate with stakeholders: Keep all relevant stakeholders informed throughout the incident response process.
- Evaluate and improve: After resolving the security incident, conduct a thorough review to identify weaknesses and implement measures to prevent future incidents.
Frequently Asked Questions
Welcome to our FAQ section on how to respond effectively to a security incident. Here, we have compiled some common questions and provided detailed answers to help you handle security incidents like a pro.
1. What steps should I take immediately after discovering a security incident?
When you discover a security incident, it's crucial to act swiftly and effectively. The first step is to isolate the affected systems or networks from the rest of your infrastructure to prevent further damage. Next, notify your incident response team and any relevant stakeholders so they can provide support and assistance. Once the initial response is underway, begin gathering information about the incident, such as logs, timestamps, and any indicators of compromise, to help with the investigation.
Afterward, it's important to assess the impact of the incident on your organization's operations, systems, and data. This will help you prioritize your response efforts and allocate appropriate resources. Remember to document all actions taken during this phase to aid in future analysis and improve your incident response procedures.
2. What role does communication play in responding to a security incident?
Communication is a critical aspect of effective incident response. From the moment you discover an incident, clear and timely communication is key to minimizing the impact and preventing panic. Start by determining who needs to be notified and what information they should receive. This may include internal teams, external partners, customers, or law enforcement authorities, depending on the nature of the incident.
Regular updates should be provided throughout the incident response process, keeping stakeholders informed of progress, actions taken, and any potential impact on operations. It's important to establish clear channels of communication, such as email distribution lists, chat groups, or conference calls, to ensure everyone involved can collaborate efficiently and exchange information seamlessly.
3. How can I ensure the preservation of digital evidence during a security incident?
Preserving digital evidence is crucial in investigating security incidents and potentially prosecuting perpetrators. To effectively preserve evidence, it's essential to create a forensically sound environment. This involves isolating affected systems, networks, or devices to prevent unintentional alteration or destruction of evidence.
Identify and document the potential sources of evidence, such as logs, network traffic captures, or memory dumps. Make sure to follow established procedures for evidence collection and use trusted forensic tools to acquire and preserve data. Label and securely store all collected evidence, maintaining a clear chain of custody to ensure its integrity and admissibility in legal proceedings if necessary.
4. How can I analyze and investigate a security incident?
Analyzing and investigating a security incident requires a systematic approach to uncover the root causes, extend of impact, and identify any vulnerabilities that may have been exploited. Begin by collecting and analyzing relevant logs, network traffic data, system artifacts, and any other available evidence.
Use various techniques, such as intrusion detection systems, endpoint monitoring, and memory forensics, to identify and understand the tactics, techniques, and procedures (TTPs) employed by the attacker. This will help you build a comprehensive timeline of the incident and determine potential countermeasures to prevent similar attacks in the future. Throughout the investigation, document your findings, maintain a central repository of information, and regularly update key stakeholders on the progress.
5. How can I improve my organization's incident response capabilities?
Improving your organization's incident response capabilities requires an ongoing effort to enhance preparedness, coordination, and efficiency. Start by conducting regular drills and exercises to test your response plans and identify areas for improvement. These exercises can simulate different types of incidents, allowing your team to practice their roles and responsibilities.
Review and analyze past security incidents, extracting lessons learned and adapting your incident response procedures accordingly. Stay up to date with the latest security threats and trends, ensuring your team is continuously trained and equipped with the necessary skills and knowledge. Finally, establish strong partnerships with external experts, such as incident response firms or cyber insurance providers, to seek guidance and support when needed.
Understanding Incident Handling and Response in Under 3 Minutes | EC-Council
Summary
When responding to a security incident, it is crucial to stay calm and act quickly. Start by assessing the situation and gathering important information. Then, notify the necessary authorities and take steps to secure any compromised systems. Communication is key, so make sure to keep affected parties informed and cooperate with any investigations. Finally, don't forget to learn from the incident and update security measures to prevent future occurrences. Remember, being prepared and taking swift action can minimize the impact of a security incident.
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote