How To Implement IT Best Practices?
Are you interested in learning how to implement IT best practices? Well, you've come to the right place! In today's technology-driven world, it's crucial for businesses and individuals to adopt and follow best practices in the field of IT. But what exactly are IT best practices and how can you implement them effectively? Let's dive in and find out!
When it comes to IT, best practices are the tried-and-true methods and techniques that have been proven to yield optimal results. They provide a framework for achieving efficiency, security, and reliability in managing and utilizing technology. From setting up secure networks to backing up data regularly, these practices are essential for the smooth operation of any IT system.
Implementing IT best practices may seem like a daunting task, but fear not! In this guide, we will walk you through the step-by-step process of implementing these practices effectively. Whether you're a business owner looking to optimize your IT infrastructure or an individual seeking to enhance your digital security, we've got you covered. So, let's roll up our sleeves and get started on the journey to IT excellence!
1. Assess your current IT infrastructure and identify areas for improvement.
2. Research industry best practices and standards relevant to your organization.
3. Develop a comprehensive IT strategy that aligns with your business goals.
4. Create clear policies and procedures to enforce best practices.
5. Train your staff on the new IT practices and monitor their adherence.
6. Continuously evaluate and update your IT practices to stay current and improve efficiency.
Follow these steps to effectively implement IT best practices and optimize your organization's IT operations.

Implementing IT Best Practices: Mastering Efficiency and Security
Technology is an indispensable part of modern-day businesses. From small startups to multinational corporations, companies rely on IT infrastructure to streamline operations, enhance productivity, and ensure data security. However, ensuring the successful implementation of IT best practices can be a complex undertaking. In this article, we will explore the key steps and strategies to effectively implement IT best practices, covering everything from creating a robust IT governance framework to fostering a culture of cybersecurity awareness.
1. Establishing an IT Governance Framework
A well-defined IT governance framework serves as the foundation for implementing IT best practices within an organization. It outlines the roles, responsibilities, and decision-making processes related to IT initiatives. The framework should align IT with business objectives, prioritize investments, and ensure compliance with regulations. Organizations can achieve this by:
- Developing an IT governance structure that includes a governing body or committee responsible for overseeing IT-related decisions.
- Defining policies and procedures that guide IT operations, such as project management, procurement, and risk assessment.
- Establishing clear communication channels between business executives, IT leaders, and stakeholders to foster transparency and collaboration.
By following these steps, organizations can create a strong foundation for implementing IT best practices and align IT strategies with business goals.
2. Prioritizing Data Security and Privacy
Data security and privacy are paramount in today's digital landscape, where cyber threats are constantly evolving. To implement IT best practices effectively, organizations must prioritize the protection of sensitive data and the privacy of their users. Here are some key considerations:
- Implementing robust access controls: Limit access to sensitive data to authorized personnel and regularly review and update user permissions.
- Encrypting data: Use encryption techniques to protect data at rest and in transit, ensuring that even if it is intercepted, it remains unintelligible to unauthorized parties.
- Regularly conducting security audits: Perform periodic assessments of IT systems to identify vulnerabilities and address them promptly.
By making data security and privacy integral to their IT practices, organizations can safeguard their assets and maintain the trust of their customers and partners.
3. Embracing Cloud Computing
Cloud computing has revolutionized the way businesses store, access, and manage data. By migrating their IT infrastructure to the cloud, organizations can leverage numerous benefits, including:
- Scalability: Scale computing resources up or down based on demand, avoiding the need for substantial upfront investments in hardware.
- Accessibility: Facilitate remote access to data and applications, enabling employees to work from anywhere and enhancing collaboration.
- Disaster recovery and business continuity: Cloud providers typically offer robust disaster recovery solutions, ensuring data backup and quick recovery in the event of a disruption.
However, organizations must carefully consider the security and compliance aspects of cloud computing and choose reputable providers that align with their specific requirements.
4. Building a Culture of Cybersecurity Awareness
While implementing the right technologies and processes is crucial, human behavior also plays a significant role in IT best practices. Building a culture of cybersecurity awareness within an organization is essential to mitigate the risk of human error and data breaches. Key strategies for promoting cybersecurity awareness include:
- Employee training: Provide regular cybersecurity training to educate employees about common threats, best practices for passwords, and how to identify and report potential security incidents.
- Creating strong policies: Develop comprehensive IT security policies that clearly outline expected behavior, acceptable use of technology, and consequences for policy violations.
- Conducting simulated phishing exercises: Test employees' susceptibility to phishing attacks by sending simulated phishing emails. This helps identify areas for improvement and provides additional training opportunities.
By fostering a culture of cybersecurity awareness, organizations can significantly reduce the risk of successful cyberattacks.
5. Regularly Updating and Patching Systems
Software vendors continuously release updates and patches to address security vulnerabilities and improve system performance. Organizations must stay vigilant in applying these updates promptly to their IT infrastructure. Regularly updating and patching systems can:
- Address known security vulnerabilities: Updates often include security patches that address vulnerabilities discovered by the vendor or reported by users.
- Enhance system performance: Updates can also optimize performance, resulting in faster and more efficient IT operations.
- Ensure compatibility and reliability: By staying up to date with the latest patches, organizations can maintain compatibility with other software and hardware and reduce system crashes or downtime.
A proactive approach to system updates and patching is crucial to mitigate the risk of security breaches and ensure optimal IT performance.
6. Utilizing Data Analytics to Drive Decision-Making
With the vast amount of data generated by IT systems, organizations can leverage data analytics to gain insights and make informed decisions. By implementing data analytics practices, businesses can:
- Identify patterns and trends: Extract valuable insights from large data sets, enabling organizations to make data-driven decisions and identify areas for improvement.
- Improve operational efficiency: Analyze data to streamline processes, optimize resource allocation, and automate routine tasks.
- Enhance customer experience: Leverage customer data to personalize interactions, anticipate needs, and provide tailored solutions.
By harnessing the power of data analytics, organizations can leverage their data as a strategic asset, driving innovation and competitive advantage.
Further Guidelines for Implementing IT Best Practices
1. Creating a Disaster Recovery Plan
A disaster recovery plan is crucial for minimizing the impact of potential disruptions on an organization's IT infrastructure. This plan typically includes:
- Identifying critical assets: Determine the key systems, data, and applications that are vital for the organization's operations.
- Backup and recovery strategy: Implement regular data backups, both on-site and off-site, and establish processes for quick data recovery in case of a disaster.
- Testing and monitoring: Regularly test the disaster recovery plan to ensure its effectiveness and monitor for any changes or updates needed.
2. Implementing ITIL Framework
The Information Technology Infrastructure Library (ITIL) is a framework that provides guidelines for IT service management. ITIL helps organizations standardize processes and ensure the efficient delivery of IT services. Key components of the ITIL framework include:
- Service strategy: Align IT services with organizational objectives.
- Service design: Design and develop IT services to meet business requirements.
- Service transition: Implement changes and manage the transition of services into the operational environment.
- Service operation: Ensure the ongoing delivery and support of IT services.
Implementing the ITIL framework can enhance IT service quality, customer satisfaction, and overall organizational efficiency.
3. Continuous Improvement through IT Audits
Regular IT audits are essential for evaluating the effectiveness and compliance of IT systems and processes. By conducting IT audits, organizations can:
- Identify areas for improvement: Analyze IT practices and identify potential gaps or weaknesses that need to be addressed.
- Ensure compliance: Assess whether IT processes adhere to legal, industry, and organizational requirements.
- Optimize IT resource allocation: Gain insights into the utilization of IT resources and identify opportunities for optimization.
By embracing continuous improvement through IT audits, organizations can proactively identify and address challenges, ensuring the ongoing effectiveness of IT best practices.
Conclusion
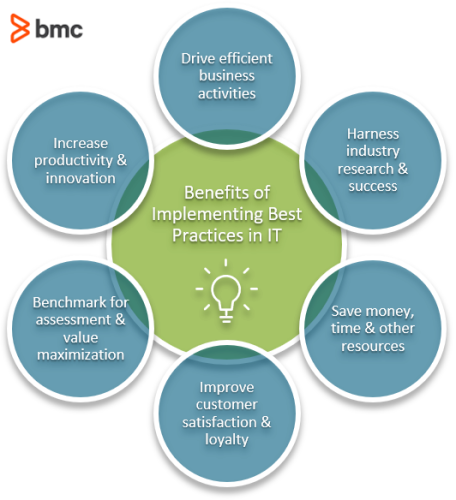
Implementing IT best practices is key to achieving efficiency, productivity, and data security within an organization. By establishing a robust IT governance framework, prioritizing data security and privacy, embracing cloud computing, fostering cybersecurity awareness, regularly updating systems, and leveraging data analytics, businesses can reap the rewards of a well-optimized IT infrastructure. Additionally, creating a disaster recovery plan, implementing the ITIL framework, and conducting regular IT audits are essential for continuous improvement, ensuring competitiveness in the ever-evolving digital landscape. By following these guidelines, organizations can navigate their IT implementation journey successfully and drive their business forward.
Key Takeaways: How to Implement IT Best Practices?
- Start by conducting a thorough assessment of your current IT infrastructure.
- Establish clear and achievable goals for your IT practices.
- Invest in robust cybersecurity measures to protect your data.
- Regularly update and maintain your software and hardware systems.
- Train and educate your staff on IT best practices to ensure consistent implementation.
Frequently Asked Questions
In today's digital age, implementing IT best practices is crucial for businesses to thrive. To help you navigate this process, we've compiled some commonly asked questions and their answers below.
Q: How can I ensure data security within my organization?
A: Implementing IT best practices for data security starts with establishing robust security policies, such as strong password requirements and regular data backups. Additionally, it's important to educate employees about the risks of phishing, malware, and other common cyber threats. Regular software updates and patches are also essential to protect against vulnerabilities that could be exploited by hackers. Working with reputable IT security providers can provide an extra layer of protection and guidance in implementing effective security protocols.
Remember, data security is an ongoing process, and it's crucial to regularly review and update your security practices to stay ahead of emerging threats. By prioritizing data security and adopting best practices, you can safeguard your organization's sensitive information and maintain the trust of your customers.
Q: How can I effectively manage my IT infrastructure?
A: Managing an IT infrastructure involves several key elements. Firstly, it's essential to establish a comprehensive inventory of all your hardware and software assets. This includes documenting details such as serial numbers, licenses, and warranties. Regularly updating and patching software, as well as monitoring and managing your network's performance, is also crucial.
Another important aspect is implementing a robust IT asset management system, which can help you track and optimize your technology resources. This involves conducting regular audits, assessing the lifecycle of your IT assets, and making informed decisions on upgrades or replacements. Outsourcing certain IT functions to specialized service providers can also help alleviate the burden of managing complex infrastructures.
Q: How can I ensure smooth IT operations during upgrades or changes?
A: When implementing IT changes, careful planning and testing are key to ensure smooth operations. Start by conducting a thorough impact analysis, identifying potential risks and dependencies associated with the changes. Create a detailed plan, including timelines, resources needed, and communication strategies to keep everyone informed.
Before rolling out the changes, it's essential to test them in a controlled environment. This allows you to identify and address any issues before impacting your live systems. Having a rollback plan in place is also essential in case unexpected issues arise during the implementation. Regularly communicating with stakeholders throughout the process is important to manage expectations and address any concerns or questions.
Q: How can I optimize my IT infrastructure for maximum efficiency?
A: Optimizing your IT infrastructure involves several steps. Start by conducting a thorough assessment of your current systems and processes, identifying any bottlenecks or areas for improvement. Utilize monitoring tools to gather data and gain insights into your infrastructure's performance and usage patterns.
Streamlining processes, automating repetitive tasks, and embracing cloud-based technologies can help enhance efficiency. Regularly evaluate and update your hardware and software to leverage the latest advancements. It's also important to collaborate with IT professionals and stay informed about emerging trends and technologies that have the potential to benefit your organization.
Q: How can I ensure user adoption of new technologies or processes?
A: User adoption is crucial for the successful implementation of new technologies or processes. Clear communication and training are key in this regard. Start by clearly outlining the benefits and purpose of the new technology or process, explaining how it will enhance efficiency or improve outcomes.
Provide comprehensive training sessions, interactive tutorials, and documentation to help users understand and embrace the change. Encourage feedback and address any concerns users may have. Consider appointing "technology champions" within your organization who can serve as advocates for the new technology and provide ongoing support to their colleagues. By investing in user adoption initiatives, you increase the chances of successful implementation and reap the benefits of your IT investments.
Summary
Implementing IT best practices can make a big difference in how technology is used in organizations. By following established guidelines, businesses can improve efficiency, security, and overall effectiveness. These practices include creating strong passwords, regularly backing up data, keeping software updated, and training employees on cybersecurity. Additionally, companies should have a plan for disaster recovery and ensure that they are compliant with relevant laws and regulations. By implementing these best practices, businesses can better protect their data, increase productivity, and stay competitive in today's digital world.
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote