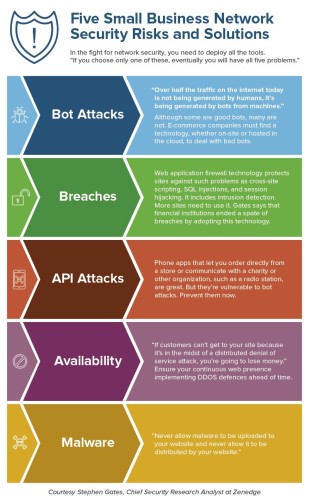
How Do IT Services Handle Network Security?
Are you curious about how IT services handle network security? Well, you're in the right place! In today's digital age, where we rely heavily on technology, ensuring the security of our networks is crucial. But how do IT services do it? Let's dive in and explore the world of network security together!
When it comes to network security, IT services play a vital role in safeguarding our sensitive information and protecting us from cyber threats. From firewalls to encryption, they employ various techniques to keep our networks safe and secure. But what exactly are these techniques? How do they work? Don't worry, we'll uncover all the answers in this article.
So, buckle up and get ready to unravel the mysteries of network security. We'll break down complex concepts into simple, easy-to-understand terms. By the end of this journey, you'll have a solid grasp of how IT services handle network security and why it's essential in today's technologically advanced world. Let's get started!
Network security is crucial for businesses. Here's a step-by-step guide on how IT services handle it:
- Analyze Network Vulnerabilities
- Implement Firewalls and Intrusion Detection Systems
- Install Antivirus and Anti-malware Software
- Set Up Access Controls and User Authentication
- Regularly Update and Patch Systems
- Train Employees on Security Best Practices
By following these steps, IT services ensure robust network security, protecting sensitive data and preventing cyber threats.
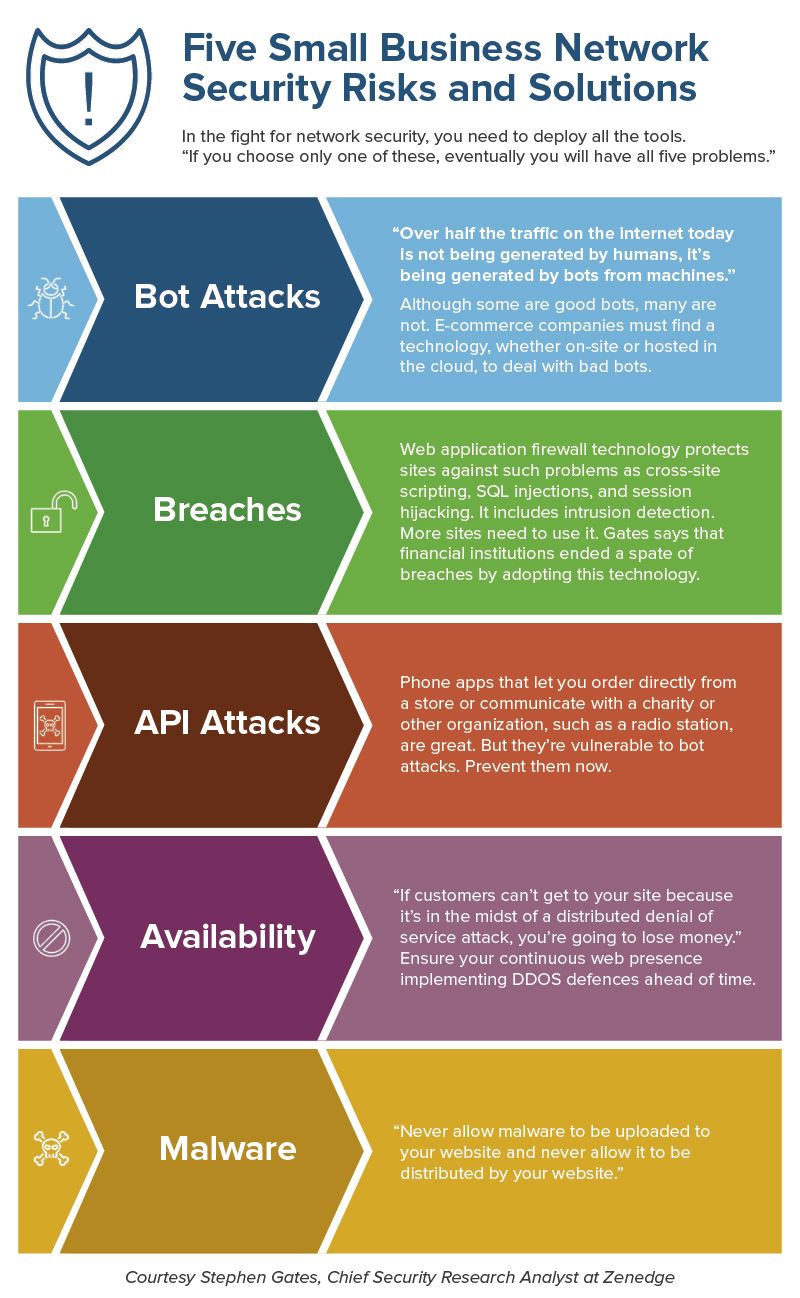
How do IT Services Handle Network Security?
Network security is a critical aspect of any organization's IT infrastructure. With the increasing complexity and sophistication of cyber threats, businesses must rely on the expertise and services of IT professionals to protect their networks from potential breaches and attacks. In this article, we will explore how IT services handle network security, the strategies and technologies they employ, and the benefits of outsourcing this task to specialized providers.
The Role of IT Services in Network Security
IT services play a crucial role in ensuring the security and integrity of a company's network. They are responsible for implementing and managing various security measures to protect against unauthorized access, data breaches, malware infections, and other cyber threats. These services work closely with organizations to assess their specific security needs, design and implement customized solutions, monitor network activity, and respond promptly to any security incidents.
One of the key tasks performed by IT services in network security is the establishment of strong firewalls and intrusion detection systems. Firewalls act as a barrier between the organization's internal network and external networks, filtering incoming and outgoing traffic based on predefined rules. Intrusion detection systems, on the other hand, monitor network traffic for suspicious activities and raise alerts or take automated actions to mitigate potential threats.
Additionally, IT services are responsible for implementing robust authentication mechanisms to prevent unauthorized access to the network. This includes the use of strong passwords, multi-factor authentication, and encryption techniques. They also regularly update security software, apply patches, and conduct vulnerability assessments to identify and address any weaknesses in the network.
Benefits of Outsourcing Network Security to IT Services
Outsourcing network security to IT services offers numerous benefits for organizations. Firstly, it allows businesses to leverage the expertise and experience of specialized professionals who have in-depth knowledge of the latest threats and security best practices. IT services continuously monitor the evolving threat landscape and stay updated with the latest security technologies, ensuring that organizations have a robust defense against emerging threats.
Furthermore, outsourcing network security can be cost-effective for businesses, especially smaller ones that may not have the resources to maintain an in-house security team. By relying on IT services, organizations can access a wide range of security tools and technologies without having to invest in expensive infrastructure and personnel training. This pay-as-you-go model enables businesses to align their security expenses with their specific needs and scale their security measures as their business grows.
Another advantage of outsourcing network security is the enhanced focus on core business activities. By entrusting network security to experts, organizations can free up their internal resources to concentrate on strategic initiatives and critical business processes. IT services can handle the day-to-day security operations, ensure compliance with industry regulations, and provide timely incident response and recovery, allowing organizations to maintain productivity and minimize disruption in the event of a security incident.
Strategies and Technologies Used by IT Services
IT services employ a range of strategies and technologies to effectively handle network security. One of the key approaches is the implementation of a layered security framework. This involves employing multiple security measures at different levels of the network to create overlapping layers of defense. These layers may include firewalls, intrusion prevention systems, antivirus software, content filtering, and encryption protocols.
In addition to layered security, IT services also focus on user awareness and training. They conduct regular security awareness programs to educate employees about the importance of adhering to security policies, recognizing phishing emails, and practicing good cyber hygiene. By empowering employees with knowledge, organizations can minimize the risk of human error leading to security breaches.
Furthermore, IT services leverage advanced threat detection and analysis technologies, such as Security Information and Event Management (SIEM) systems and behavior analytics. SIEM systems collect and analyze data from various network sources to identify patterns and anomalies that could indicate a potential security incident. Behavior analytics, on the other hand, monitor user behavior and flag any deviations from normal patterns, helping detect insider threats or compromised accounts.
Conclusion
Network security is a complex and ever-evolving field that requires specialized knowledge and expertise. By relying on IT services, organizations can ensure the confidentiality, integrity, and availability of their networks, safeguarding sensitive data and mitigating the risk of financial and reputational damage. Outsourcing network security to IT services offers benefits such as access to expert resources, cost-effectiveness, and the ability to focus on core business operations. With the right strategies and technologies, IT services play a vital role in protecting organizations from cyber threats in today's digital landscape.
Key Takeaways: How do IT services handle network security?
- IT services ensure the security of computer networks and systems.
- They use firewalls, antivirus software, and encryption techniques to protect against unauthorized access.
- Regular software updates help maintain network security.
- IT services conduct regular security audits to identify and fix vulnerabilities.
- Employee training on safe internet practices is crucial for network security.
Frequently Asked Questions
In today's digital age, network security is a top concern for businesses. IT services play a crucial role in handling network security by implementing various measures to protect sensitive information and prevent unauthorized access. Here are some commonly asked questions about how IT services handle network security:
1. How do IT services prevent unauthorized access to networks?
IT services employ several methods to prevent unauthorized access to networks. One of the key measures is implementing strong and complex passwords for all users. This ensures that only authorized individuals can access the network. Additionally, IT services also use firewalls to create a barrier between internal networks and external threats. Firewalls analyze incoming and outgoing network traffic, blocking any potentially harmful or unauthorized connections. Regular security audits and vulnerability assessments are also conducted to identify and address any potential weak points in the network security.
Furthermore, IT services often use encryption techniques to protect data transmission over networks. Encryption converts plain text into unreadable ciphertext, making it extremely difficult for attackers to decipher the information. By combining these preventive measures, IT services can significantly reduce the risk of unauthorized access to networks.
2. What steps are taken to ensure data privacy in network security?
IT services take several steps to ensure data privacy in network security. One of the primary measures is implementing access controls that restrict information access to authorized personnel only. This includes securing data through user authentication, such as usernames and passwords, and implementing role-based access control (RBAC) systems. RBAC ensures that users have access only to the data and resources necessary for their roles, minimizing the risk of unauthorized access to sensitive information.
In addition, IT services also implement data encryption techniques to protect sensitive information. Encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties unless they possess the decryption keys.
3. How do IT services handle network security updates and patches?
IT services regularly update and patch network security systems to address vulnerabilities and stay protected against emerging threats. They closely monitor security trends and stay updated with the latest patches released by software and hardware vendors. These patches fix vulnerabilities and strengthen the overall network security.
IT services follow a systematic approach for handling updates and patches. They first assess the impact and relevance of the update or patch to their specific network infrastructure. Then, they carefully plan and schedule the implementation to minimize disruption to the network and ensure a smooth transition. IT services also conduct thorough testing before deploying the updates or patches to ensure compatibility and stability.
4. How do IT services protect businesses from malware and viruses?
IT services implement various measures to protect businesses from malware and viruses. One of the primary methods is installing and updating reliable antivirus software across all devices and systems in the network. Antivirus software scans for and removes any known malware or viruses, protecting the network from potential threats.
IT services also employ email filtering systems to prevent phishing attacks and block suspicious attachments or links that may contain malware. They often educate employees about safe online practices and the importance of not opening or clicking on suspicious emails or links. Regular system scans and malware threat assessments are conducted to detect and remove any threats that may have bypassed the initial security measures.
5. How do IT services prepare for and respond to security breaches?
IT services understand that despite preventive measures, security breaches can still occur. In preparation, they establish incident response plans with clear steps and procedures to mitigate the impact of a breach. These plans include details on personnel responsibilities, communication protocols, and the steps to isolate affected systems to prevent further spread of the breach.
When a security breach occurs, IT services immediately initiate their incident response plan, working swiftly to identify the breach's source and minimize any potential damage. They also collaborate with relevant stakeholders, such as legal teams and law enforcement agencies, to ensure the appropriate actions are taken. After the breach is contained and mitigated, a thorough analysis is conducted to identify any weaknesses in the network security and implement additional measures to prevent future breaches.
Security Services
Summary
So, in a nutshell, IT services play a crucial role in network security. They protect your computer systems from hackers and viruses, keeping your data safe. They use firewalls, encryption, and other tools to create a strong defense against cyber threats. It's like having a security guard for your digital world!
But remember, staying safe online is a shared responsibility. You need to do your part too by using strong passwords, being cautious about clicking on suspicious links, and keeping your software up to date. By working together, we can keep our networks secure and enjoy all the benefits of the digital age!
Recent Posts
- How Does GPON Improve Network Efficiency?
- What Are The Advantages Of GPON?
- What Are The Benefits Of IT Outsourcing?
- What's The Deal With Ransomware Attacks?
- Are GPON Providers Widely Available?
- What's GPON's Impact On Bandwidth?
- Why Is Multi-Factor Authentication Important?
- How To Ensure Data Privacy Compliance?
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies Call For Quote
Call For Quote