
What's The Coverage Like With Philippine Mobile Providers?
Looking for information about the coverage of mobile providers in the Philippines? Wondering how good the signal is? Well, you've come to the right place!
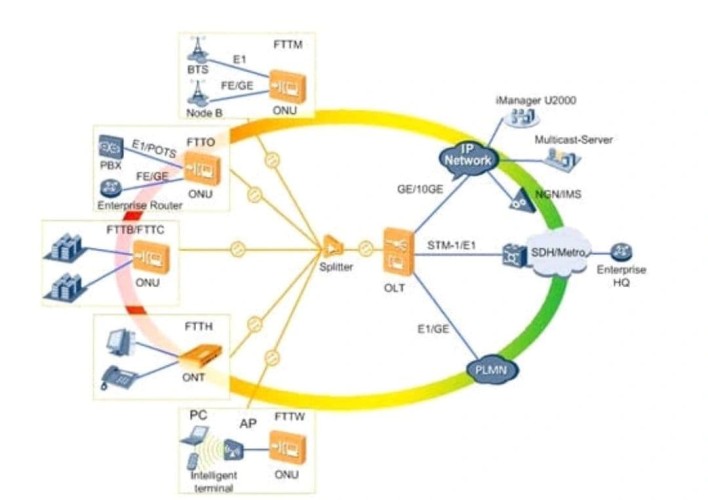
Is GPON Affected By Weather Conditions?
Are you curious to know if GPON, the technology behind internet connection, gets affected by weather conditions? Well, you're in the right place!
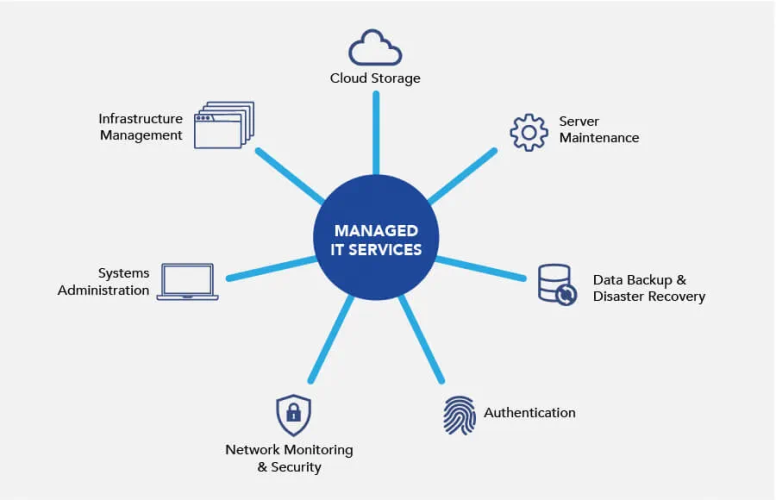
Do Managed IT Services Offer Mobile Support?
Do you ever wonder if your IT services are equipped to support your mobile devices? Well, look no further! Managed IT services might just be the solution you're looking for.

Why Is 24/7 IT Support Crucial?
Picture this: it's the middle of the night and your computer crashes. You're stuck, frantically searching for a solution. That's where 24/7 IT support comes in. But why is it crucial? Let's find out!
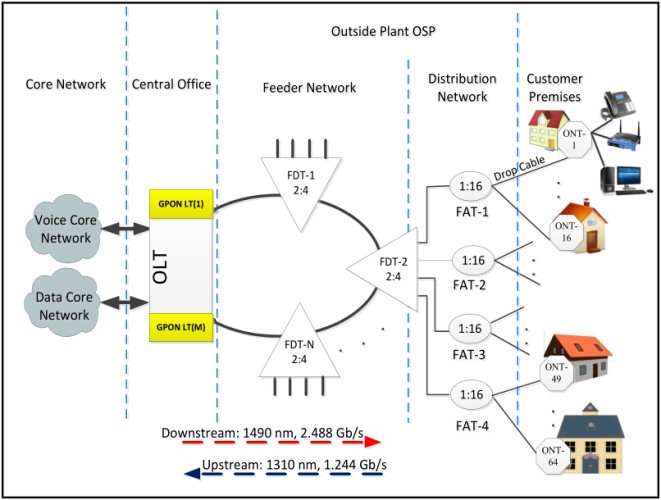
What Are GPON Network Architecture Types?
Hey there! Are you curious about GPON network architecture types? Well, you've come to the right place. In this article, we'll uncover the different types of GPON network architectures and explore what makes them unique. So, what exactly is GPON? GPON

Do Providers Offer Business Packages In The Philippines?
Looking to take your business to the next level in the Philippines? Well, you're in luck! Do providers offer business packages in the Philippines? Absolutely! In fact, there are plenty of providers in the country that cater specifically to the needs of b

What's The Role Of IT Services In Disaster Recovery?
Introducing the world of IT services in disaster recovery! So, what's their role? Well, imagine a catastrophic event like a natural disaster or a cyber attack that wreaks havoc on a company's systems. That's when IT services step in to save the day. Yo
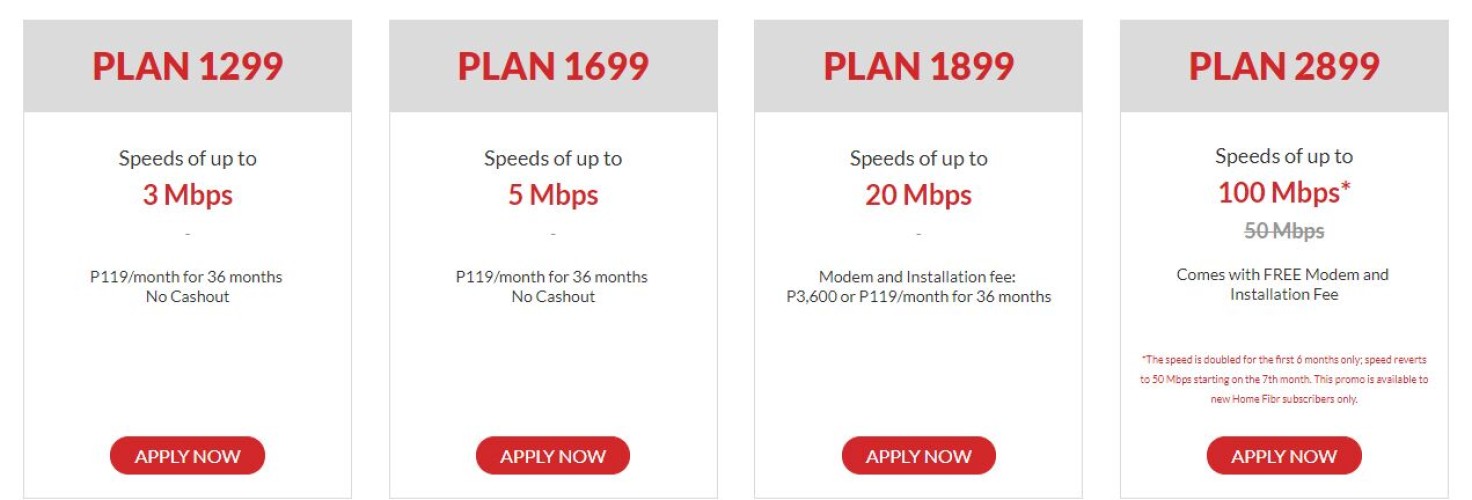
Any Tips For Finding The Best Service Providers In Manila?
Planning to find the best service providers in Manila? Wondering where to start? Well, you've come to the right place! In this article, we've got some tips that will help you navigate the bustling city and find the top-notch services you're looking for. W

Why Do Businesses Need IT Support?
In today's fast-paced world, technology is everywhere, and businesses rely on it more than ever. From managing data to ensuring cybersecurity, IT support plays a crucial role in keeping businesses up and running smoothly.
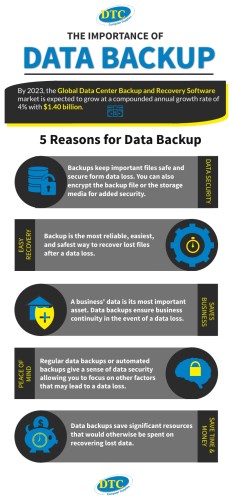
Why Is Data Backup Important?
Data backup might not sound like the most exciting topic, but let me tell you, it's super important! So, why is data backup important? Well, picture this: you're working on a school project or creating that cool video game you've been dreaming up, and sud
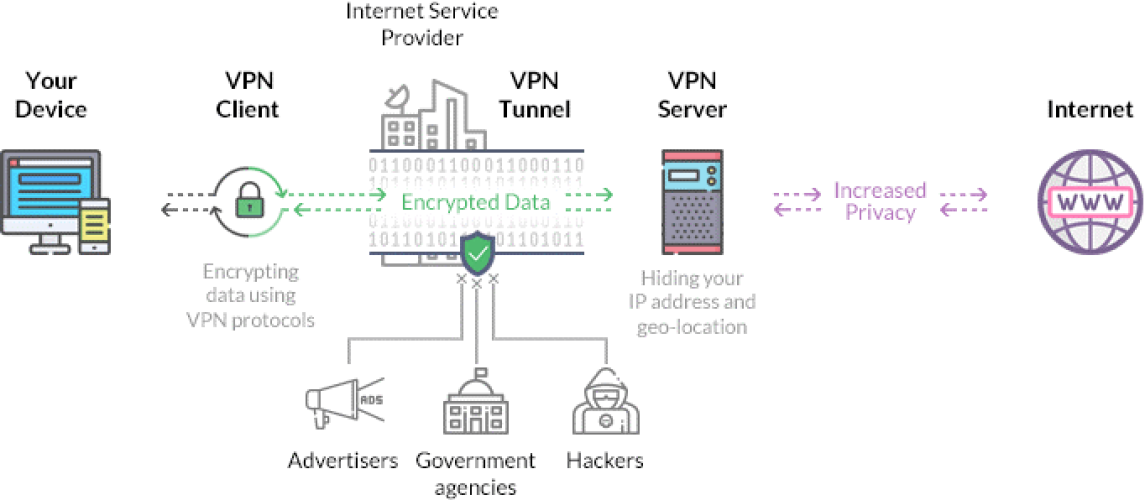
What Is A VPN And Why Do I Need It?
Picture this: you're surfing the web, exploring cool stuff, watching videos, and chatting with friends. But have you ever wondered if your online activities are truly secure? Well, here's where a VPN comes into play. So, what is a VPN, and why do you need
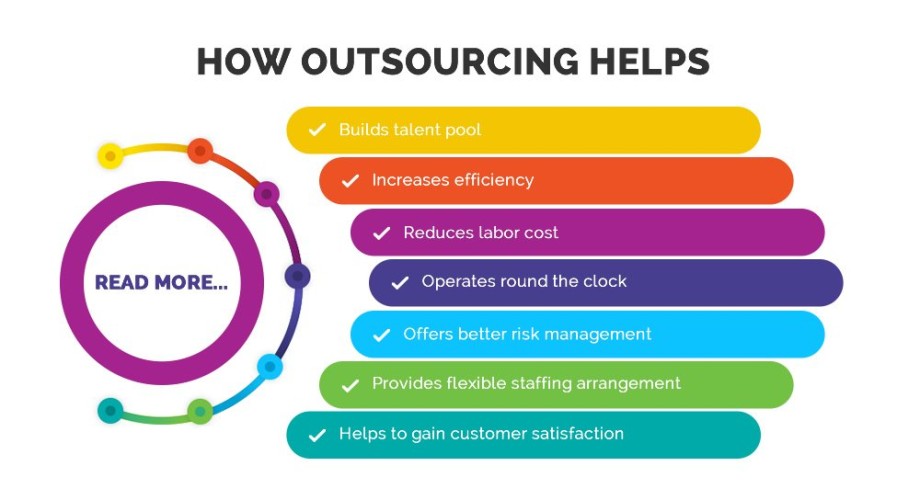
What Are The Benefits Of IT Outsourcing?
What are the benefits of IT outsourcing? Well, let me tell you, it's like having your own super-powered team of experts without the hassle of hiring and managing them yourself. Imagine being able to focus on your core business while skilled professionals
 Blogs
Blogs Infographics
Infographics Videos
Videos Podcasts
Podcasts Case Studies
Case Studies